Pentest week 6, hunter2
Penetration testing week 6
This week on the course agenda is password cracking with hashcat and overall how to crack passwords for different services and files.
Links to exercise sections
- a) Creating and cracking hashes
- b) Hydra against ssh
- c) Bruteforcing HTML forms
- d) Making a wordlist
- e) Cracking zip-password protection
- f) PDFCrack
- g) HTB machines
- z) Reading/listening/video summary
z) Reading/listening/video summary
Taylor et al 2018: The Art of Hacking: Hacking User Credentials
- Encrypt passwords and limit access to only those who truly need it to stay safer
- salt the hashes to make cracking harder
- two-factor authentication makes exploitation of cracked and found passwords very difficult
- Many machines and services are running with the default passwords that can be searched for easily
- Credentials can for example be sniffed, captured with a MITM attack or bruteforced
- Passwords are hashed and can be bruteforced from the hash by trying to hash different cleartext credentials
- using GPUs makes cracking very fast
- Many wordlists are public that make cracking common passwords easy
- Common tools
- John The Ripper
- hashcat
0xfd: HTB: Union
- A Linux machine
- nmap scan found http port open
- website has a single text input form
- gives a link to another similar page
- directory enumeration fives no useful results
- one form seems to be vulnerable for injection but is filtered
- union injection works
- a flag is found in db that opens ssh port when submitted
- SQL has read-file permissions so it can be used to read /etc/passwd and website source files
- one file has credentials that work for ssh
- user flag is now found
- one page has command injection vulnerability through a request header
- create a reverse-shell as another user
- user has sudo privileges
- root flag now accessible
a) Creating and cracking hashes
The task is to create three hashes with different programs and then crack them with hashcat and a selfmade small dictionary. I'll use
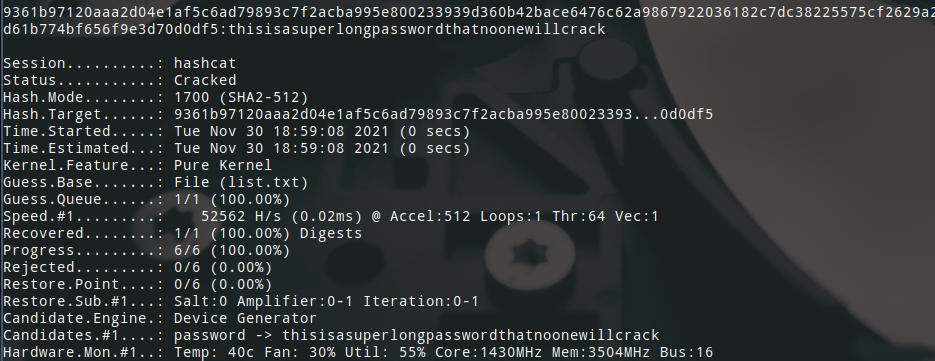
- SHA512 (mode: 1700)
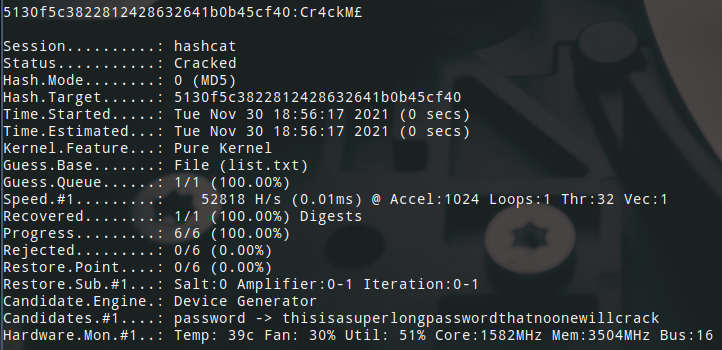
- md5 (mode: 0)
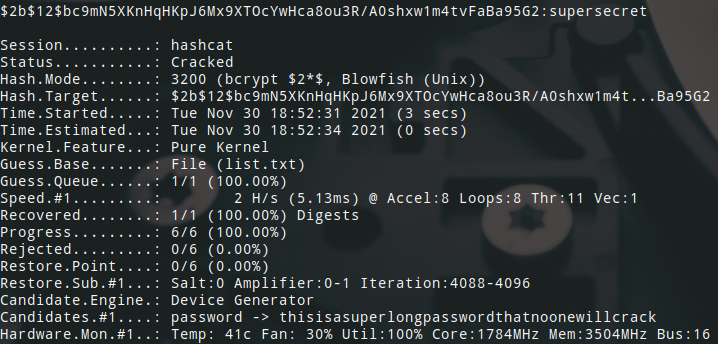
- bcrypt (mode: 3200)
I made the md5 and bcrypt hashes with a python oneliner and the sha512 hash with the sha512sum command-line tool.
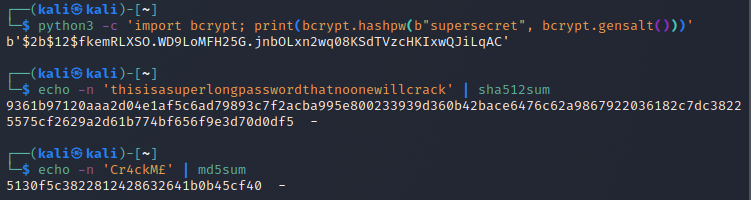
I then ran hashcat once for each hash with the corresponding mode with a very short 5 line list of passwords.
b) Hydra against ssh
Before starting to use hydra anywhere I read a bit from the manpage. The options I need to run it are
- target: attack target
- service: service protocol to attack over
- -l or -L: login string or file to try
- -p or -P: password string or file to try
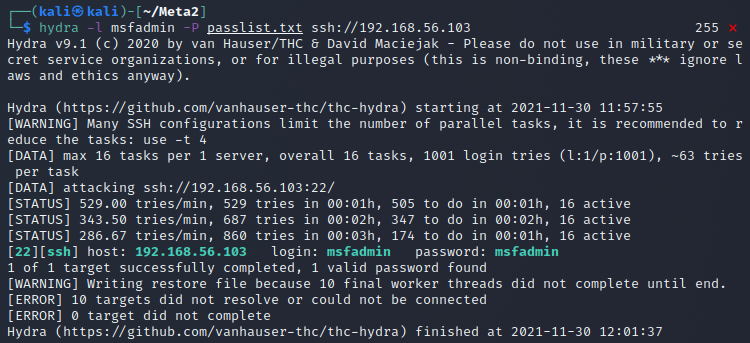
I started my Metasploitable 2 machine on the VBox host-only network and copied a small list of passwords and added the known password for msfadmin into it somewhere so that I could make sure it works right. I ran hydra with hydra -l msfadmin -P passlist.txt ssh://192.168.56.103 and after 4 minutes I got the results. The credentials were found! Though this seemed really slow so I think cracking over ssh is not really worth it if you're in a hurry, or even if you're not.
c) Bruteforcing HTML forms
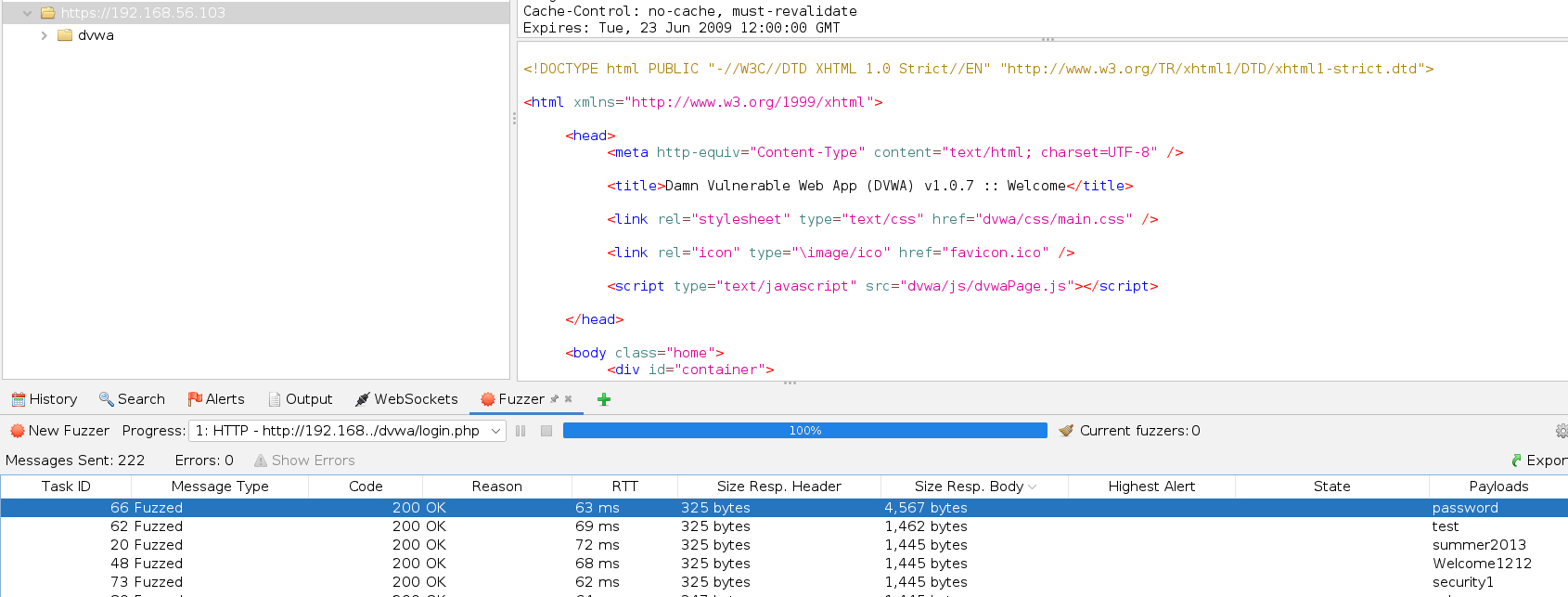
The form that I will be trying to crack is the login form of DVWA of Metasploitable 2. I will test bruteforcing the default user (admin) with a small wordlist that actually contains the correct password to see if I can get a response of a successful login.

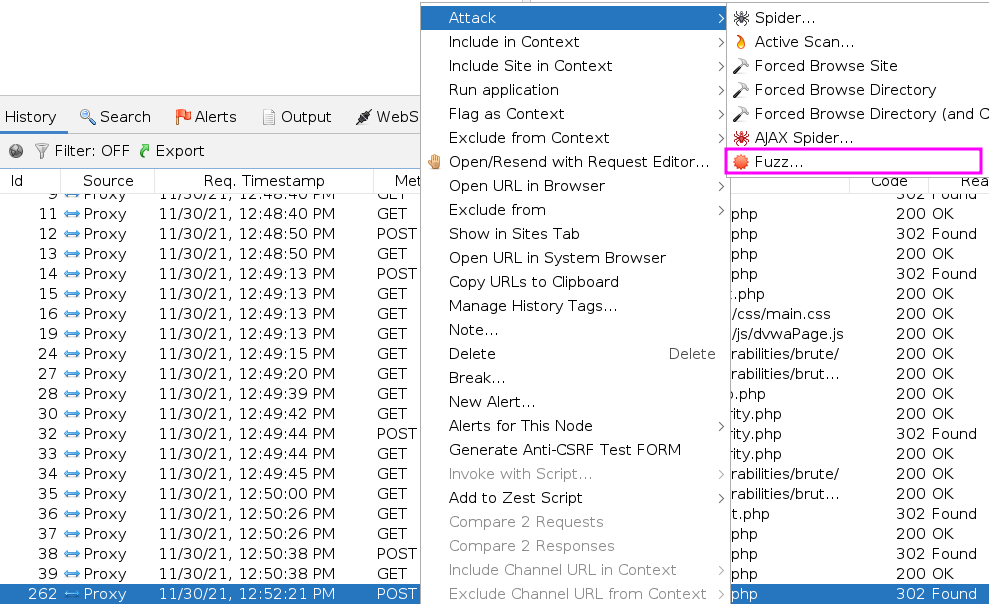
I first took the POST request from history and from the right-click menu chose attack/fuzzing.
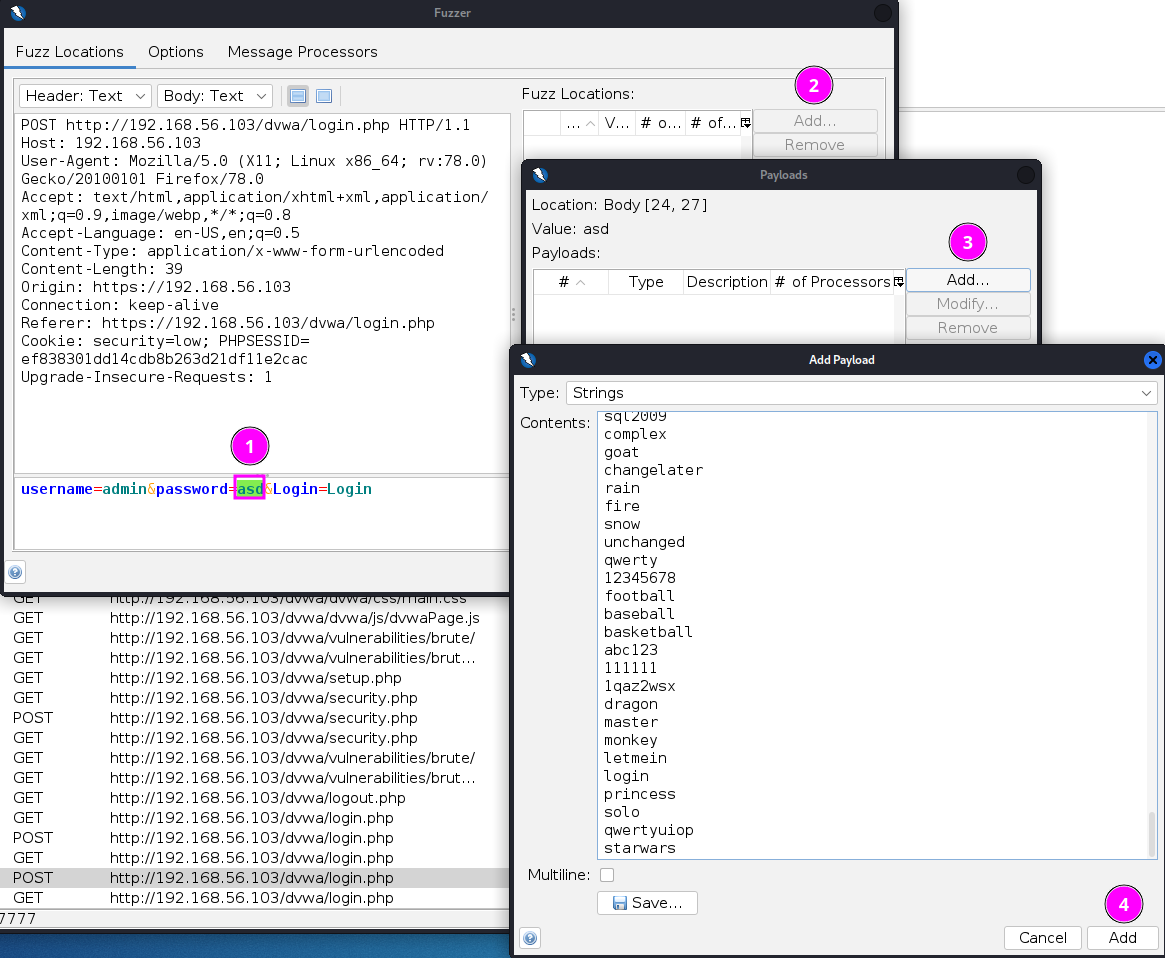
Then I chose the value to modify and added the wordlist to be used.
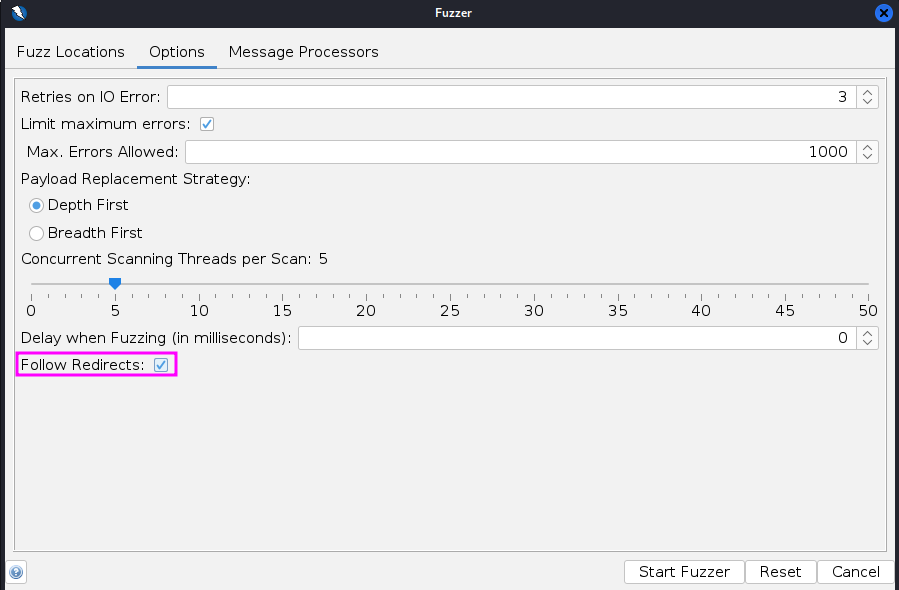
I added the option to follow redirects so that I could get the response from the landing page after a successful login.
I then ordered the requests by response body size and one stood out that was then the right password.
d) Making a wordlist
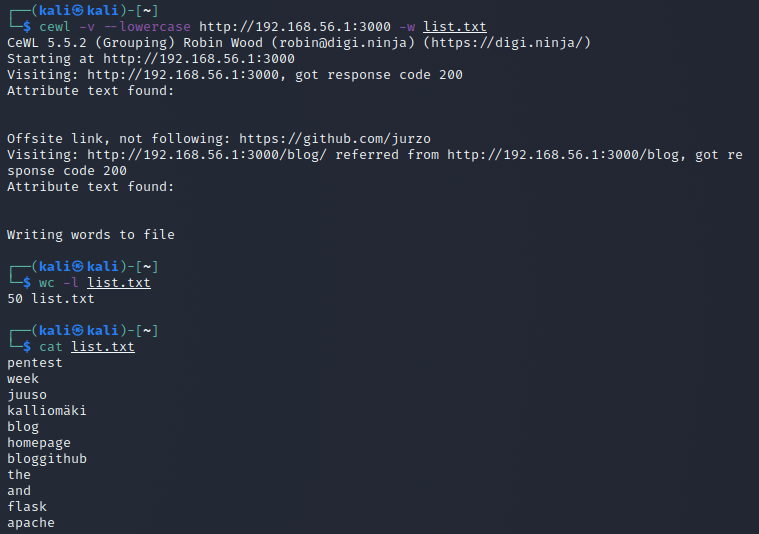
For making a wordlist based on a website I found cewl after some googling. I will be trying to make a wordlist out of my blog site by running it locally and running the script cewl -v --lowercase http://192.168.56.1:3000 -w list.txt.
- the -v flag gives verbose output during runtime
- the --lowercase flag makes all retrieved words lowercase
- the -w flag writes the output to a file
This produced a 50 word long list.
e) Cracking zip-password protection
Before trying to crack a zipfile password I have to create the file. I create some files with something inside as I found out that this does not work with empty files.
echo -n 'aslfkjafdsgoiuahlsdfkgjhasoidfgbalsdfjhkgyaoskdfngbalksdjgadsfg' > file.txt
for i in `seq 1 10`; do cat file.txt > file$i.txt; done
zip -e secret.zip ./* #password=changelater
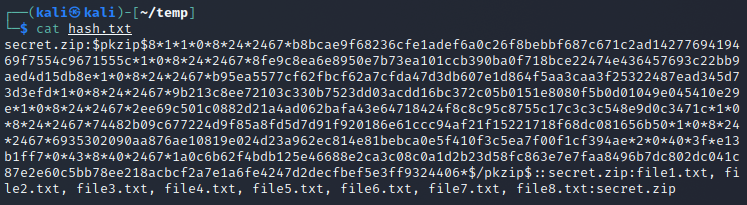
Now I used zip2john, a preinstalled tool on Kali to generate a hashfile that I could then start cracking: zip2john secret.zip > hash.txt.
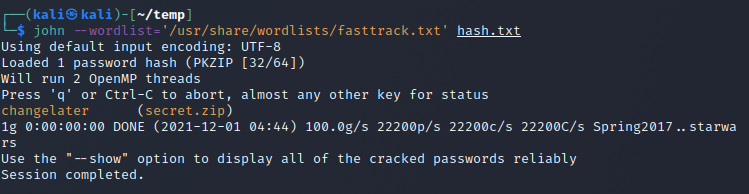
I then ran johnjohn --wordlist='/usr/share/wordlists/fasttrack.txt' hash.txt and the password was cracked.
f) PDFCrack
For this task I went online and added a password from rockyou.txt to a pdf file. Then I used this python script to extract a hash from the pdf so that I could start cracking it.
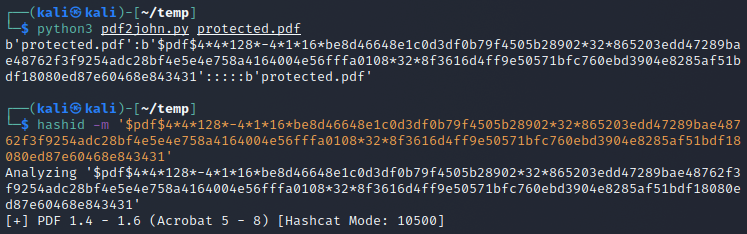
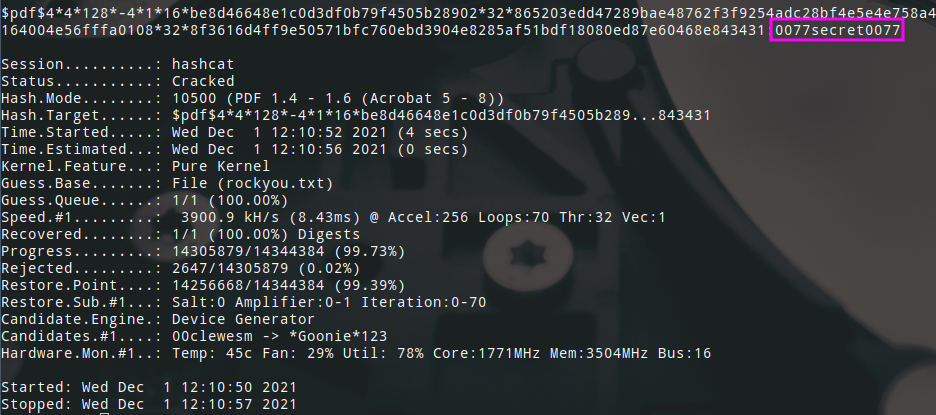
Now that I had the hashcat mode and the hash I could just start cracking. I just ran hashcat with mode 10500 and the rockyou wordlist and it was cracked in no time.
g) HTB machines
My take on the HTB machine Secret can be found here.
Sources
- Course: https://terokarvinen.com/2021/penetration-testing-course-2021-autumn/
- Taylor et al 2018: The Art of Hacking: Hacking User Credentials: https://learning.oreilly.com/videos/the-art-of/9780135767849/9780135767849-SPTT_06_00
- PDFCrack: http://pdfcrack.sourceforge.net/
- 0xfd: HTB: Union: https://0xdf.gitlab.io/2021/11/22/htb-union.html